Windows 10 Upgrade Phishing Emails
Since Microsoft began offering Windows 10 as a free upgrade for Windows 7, 8, and 8.1 users, I’ve received emails from readers stating that they were receiving suspicious emails that instructed them to download a special tool to start the upgrade process. These are in fact phishing emails that are sent to unsuspecting computer owners, where they may trick victims into thinking that this is their notification from Microsoft to upgrade to Windows 10.
Windows 10 Phishing Examples
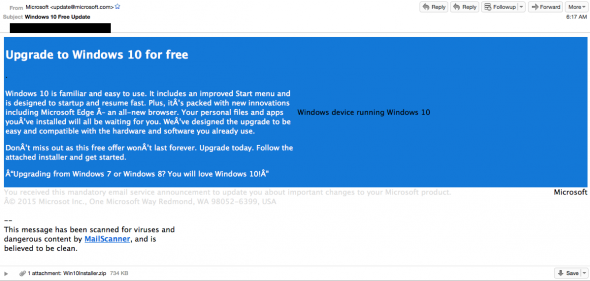
Here’s an example of one phishing email:
These phishing e-mails are basically attempts to get people to download and install harmful software to their computers. Once installed, these pieces of software encrypt the user’s personal files, including documents, pictures, and more, to hold it ransom in hopes that the unsuspecting victim will pay money to regain access to their files.
It’s important to note that malicious software are smart enough to evade and bypass any locally installed anti-virus software. Assuming that the user is gullible enough to have clicked on the phishing email, then they will wreck havoc on their systems because they were in fact installed by the owner of the computer, which means that they were probably installed with administrator rights.
If the user does not comply with the ransom in the given period of time, the software will then initiate a self-destructing operation that will prevent any future release of the blocked files.
Removing Ransomware Software
Ransomware software can be very difficult to remove, and there’s traditionally only two available options that are available. The best option is to restore from a recent backup, otherwise pay the fee and hope the hijackers deliver the decryption key.
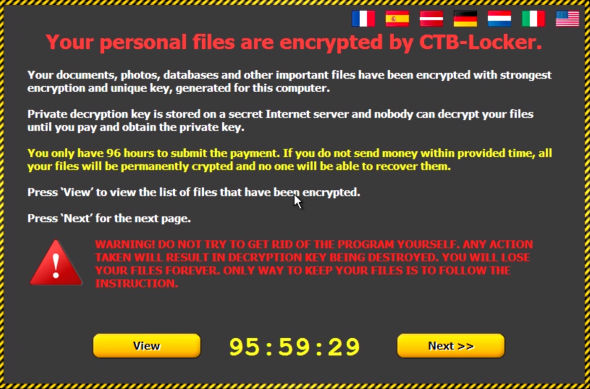
Some ransomware software variants are called CryptoLocker, Crowti, Cryptowall to name a few. The following image shows a phishing ransomware campaign that gives the users a 96-hour window to deliver payment, but other time intervals may be seen in the future.
Researchers at Cisco TALOS spotted spam carrying an archived attachment from an email address in Thailand spoofing update at Microsoft[.]com:
“There are several characters that don’t parse properly,” Cisco TALOS researchers wrote in a blog post. “This could be due to the targeted audience, a demographic using a non-standard character set, or the character set the adversaries were using to craft the email.”
“Two other features in the message attempt to add some legitimacy to the campaign, the first being a disclaimer using similar language to what Microsoft regularly uses, and the other being a notification that the email was scanned by ‘MailScanner’ and is clean of malware.”
First, be very careful with any e-mail claiming to be from Microsoft about a Windows 10 upgrade. Although you may want to test the link to see if it goes to a Microsoft website, it’s better not to click on any suspicious image, link, or attachment. Instead, go directly to the Microsoft website for more information:
As a final reminder, legitimate companies almost never use unsolicited e-mails. Never provide any personal information over the phone or via e-mail, and treat all unsolicited e-mails and phone calls with great skepticism.
If you or anyone you know has already clicked on links and downloaded any software, the only good advice I can give you is to completely shut down the computer, disconnect it from any Internet connections, and immediately contact a local computer specialist for advanced technical support . Unfortunately, in most cases, this may come too late and your files will most likely already be encrypted. Also, be sure to check your backups and set one up now, if you haven’t already.