Windows 10 Creators Update Delivers a More Secure Edge

In today’s Ask the Admin, I will look at how Microsoft is providing a more secure browsing experience with Edge in the Windows 10 Creators Update.
Microsoft Edge took a bit of a bashing at last week’s annual Pwn2Own competition. It came out on top as the most hacked browser. Considering how Edge is positioned as more secure than Chrome and Firefox, this is something of an embarrassment for Microsoft. On day one of the contest, Tencent Security – Team Ether managed to break out of the Edge sandbox. They were using an arbitrary write-in within the browser’s JavaScript engine, Chakra. On day two, Tencent Security – Team Lance, with some help from Team Sniper, exploited a Use-After-Free (UAF) vulnerability in Chakra. This elevated privileges to SYSTEM using another UAF vulnerability in the Windows kernel.
On day three, 360 Security exploited a heap overflow in Edge. Doing so helped them escape from a VMware Workstation virtual machine (VM). This was the first time anyone has performed a full VM escape at the competition. Edge was targeted again by Richard Zhu. He used two separate UAF flaws to escalate to SYSTEM using a buffer overflow in the Windows kernel.
Considering these results, it may be tempting to think that Edge is not as secure as Microsoft would have us believe. It is important to remember that Mac OS X and Linux were also successfully hacked. Also, keep in mind that the zero-day flaws in Edge will be patched by Microsoft in the coming weeks. Other factors, such as whether the attacks were carried out as Protected Administrators or standard users, might also affect whether the zero-days can be successfully exploited. But in what seems like good timing, the forthcoming Windows 10 Creators update will bring improvements to Edge security.
Microsoft Edge Sandbox
Like all Universal Windows Platform (UWP) apps, Edge runs in a sandbox environment, providing isolation from the OS and other applications. Edge processes are isolated in seven different sandboxes or application containers.
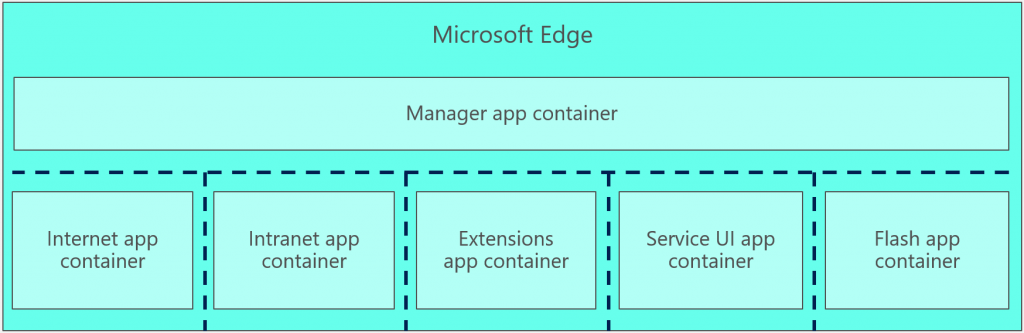
The Edge app container is denied access to secured objects unless the object has an ALLOW access control entry (ACE) for a Capability, AppID, or AC SID. The requesting app container will have the object SID (Capability or AppID) in its security token. The AC SID (ALL APPLICATION PACKAGES) is a wild card that allows all app containers to access a resource. Most WinRT APIs can be accessed using the AC SID.
Reducing the Attack Surface in the Creators Update
In the Creators Update, Microsoft has acknowledged that Edge needs a stronger sandbox than other UWP apps. It has been modified so that it is completely isolated from Windows Runtime (WinRT) APIs. All resources that formerly held apps in a sandbox can now be granted access. This is done by requiring that the Edge app container explicitly use a matching Capability or AppID SID. And the AC SID will no longer be enough to grant access.
To make this security model work, Microsoft created specific Capabilities. This provided Edge with just enough access to achieve the required functionality, considerably reducing the attack surface. Due to it being a common target, a tuned app container is also used to isolate Flash.
The use of broker interfaces, which provide access to resources based on policy, has also been reduced. Brokers run outside the app container, which makes them vulnerable to attack. The content process app container removes many brokers. Those that remain are subject to exploit mitigation technologies. This should make brokers harder to exploit. The Chakra JIT code generator and Flash were moved out-of-process and placed in specially-tuned app containers. This occurred because they broke when Arbitrary Code Guard (ACG) mitigation was applied to the content process.
The work Microsoft has carried out makes it harder for attackers to break out of the Edge app container. There has been a 90 percent reduction in access to WinRT and DCOM APIs. Other benefits include:
- A 100 percent reduction in access to MUTEXes — cannot cause a resource to hang
- A 70 percent reduction in access to events and symlinks
- A 40 percent reduction in access to device drivers
In this article, I explained how the changes Microsoft has made to Edge in the Creators Update will improve security.



