Why You Should Use Microsoft’s Active Directory Tier Administrative Model
In this Ask the Admin, I’ll explain what Microsoft’s AD tier administrative model is and how it can improve security.
Access controls are an important defense mechanism for sensitive information systems. But access controls can be ineffective if poorly implemented. One bad decision can lead to a compromise. You only have to look at many organization’s Active Directory (AD) to realize that little thought has been put into how to grant access to the directory, domain controllers (DCs), and other sensitive assets. It is common to find IT support staff with domain administrative privileges, domain admin accounts used to log in to users’ PCs, and administrative user accounts and passwords shared across multiple devices.
Microsoft has been working to reduce the impact of breaches caused by poor access controls. For example, Windows 10 Credential Guard aims to protect domain credentials on compromised PCs. The new Azure Confidential Computing initiative uses Trusted Execution Environments (TEEs) to protect unencrypted data as it is being processed.
For more information on Azure Confidential Computing, see Microsoft Announces Azure Confidential Computing on the Petri IT Knowledgebase. You can read about Windows 10 Credential Guard on Petri here: Windows 10 Enterprise Feature: Credential Guard.
Active Directory Administrative Tier Model
Despite the security features Microsoft is including in Windows 10 and Windows Server 2016, implementing proper access controls is still an important defense. The tiered administrative model aims to help organizations to better secure environments. The model defines three tiers that create buffer zones to separate administration of high-risk PCs and valuable assets like domain controllers.
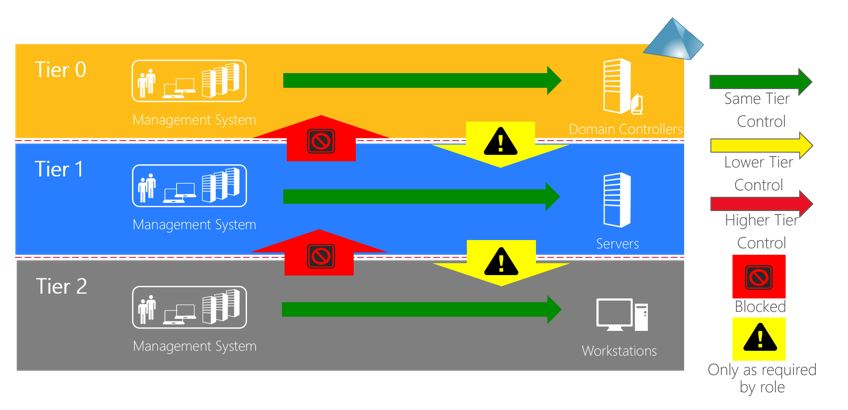
Tier 0 is the highest level and includes administrative accounts and groups, domain controllers, and domains that have direct or indirect administrative control of the AD forest. Tier 0 administrators can manage and control assets in all tiers but only log in interactively to Tier 0 assets. I.e. a domain administrator should never interactively log in to a Tier 2 asset.
Tier 1 is for domain member servers and applications. Accounts that control these assets have access to sensitive business data. Tier 1 administrators can access Tier 1 or Tier 0 assets (network logon) but can only manage Tier 1 or Tier 2 assets. Tier 1 administrators can only log on interactively to Tier 1 assets.
Tier 2 is for end-user devices. For example, helpdesk staff would be part of this tier. Tier 2 administrators can access all tier assets (network logon) as necessary but can only manage Tier 2 assets. Tier 2 admins can log in interactively to Tier 2 assets.
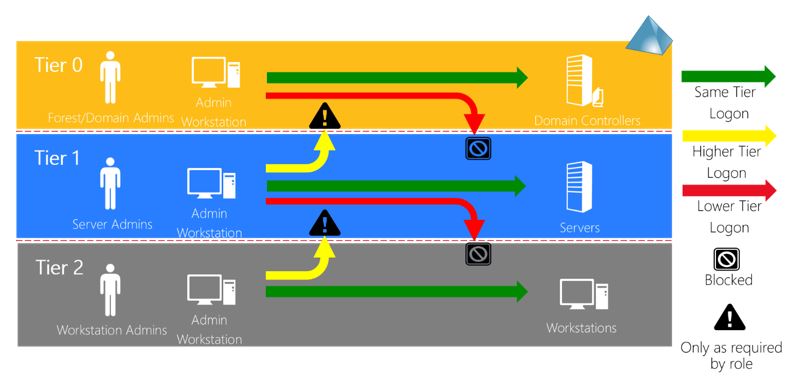
The three tiers increase the cost for an attacker trying to compromise sensitive systems. You should consider that a user that has full access to all Tier 2 assets could get access to assets in a higher tier. The tiered administrative model makes it harder for a hacker to move from a Tier 2 to a Tier 0 asset but doesn’t make it impossible.
Security Best Practice
Understanding the tiered model gives you a better insight into Microsoft’s security best practices. For example, a Privileged Access Workstation (PAW) that is used by a domain administrator is also considered a Tier 0 asset. A Tier 0 administrator must use a Tier 0 PAW to manage other Tier 0 assets, such as domain controllers because the account will be a member of a highly-privileged domain or forest group.
The tiered administrative model isn’t hard to implement. It does require additional resources, like PAWs, and some planning in how to manage access and control between the tiers. It is achievable for most organizations and goes a long way to implementing effective access controls that will keep hackers from compromising sensitive systems.
For more information on how to manage end-user devices without using domain administrative privileges, see Manage Workstations Without Domain Admin Rights on Petri.
Follow Russell on Twitter @smithrussell.



