Managing security is probably the number-one headache for Windows administrators. Between the file system, registry, and services, IT Pros have their hands full managing access control, especially if they want to script from the command line. There are certainly a number of command line tools to manage these different areas, but because I’m an old-school kind of guy, I tend to fall back to an old resource kit tool: SubInACL, or subinacl.exe, the veritable Swiss Army knife when it comes to managing permissions.
SubInACL: Download, Limitations, and Requirements
Because it’s not part of the operating system, you will first need to download the subinacl.axe tool. The download file is an MSI file which will install by default to C:\Program Files (x86)\Windows Resource Kits\Tools\. The tool is a single file that you can move to C:\Windows\System32 so that you always have access to it.
C:\Program Files (x86)\Windows Resource Kits\Tools>move subinacl.exe c:\windows\system32
Note: I need to point out that, officially, subinacl.exe is not supported on anything later than Windows Server 2003. But in my experience, I’ve never had a problem running it on newer operating systems. Still, I strongly recommend first testing in a non-production environment and understand that Microsoft may not be able to help you if you run into problems.
To use subinacl.exe, the assumption is that you have administrator credentials. If you are delegating administration using subinacl.exe, you will need to make sure the account has the following privileges:
- SeBackupPrivilege (Back Up Files and Directories)
- SeChangeNotifyPrivilege (Bypass Traverse Checking)
- SeRestorePrivilege (Restore Files and Directories)
- SeSecurityPrivilege (Manage Auditing and Security Log)
- SeTakeOwnershipPrivilege (Take Ownership of Files or Other Objects)
- SeTcbPrivilege (Act As Part of the Operating System)
Getting Help in SubInACL
I won’t sugar coat it: Subinacl.exe is a very complex tool. But fortunately the command help is thorough. One way to access the help is to open the subinacl.htm file (C:\Program Files (x86)\Windows Resource Kits\Tools\subinacl.htm) that should also have been installed. I encourage you to take the time to read it.
From the command prompt you can get help directly from the tool.
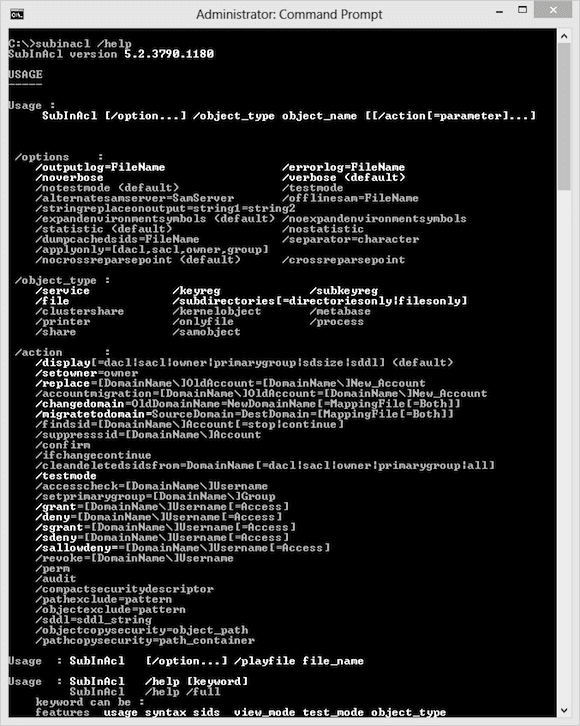
C:\> subinacl /help
You can ask for help on any keyword or command element. Try these help commands after you’ve installed subinacl.exe.
C:\>subinacl /help syntax C:\>subinacl /help /testmode C:\>subinacl /help /keyreg C:\>subinacl /help /display
Or to see really complete help run this:
C:\>subinacl /help /full
Basic Syntax
To use SubInACL, there are three components to a command. I’ll go over each one.
SubInACL /Option <options> /object <object> /action
Options
The default option is simply to display what the command terms “statistic” in verbose mode. The statistic is how long it took the command to run. After running a command you’ll see something like this:
Elapsed Time: 00 00:00:00 Done: 1, Modified 0, Failed 0, Syntax errors 0 Last Done : \\serenity\work
If you don’t need this you can turn it off with /nostatistic. You may also want to turn off verbose mode (/noverbose) or direct output to a text file (/outputlog=mylog.txt).
Objects
Subinacl.exe can be used against a number of different object types such as files, shares, printers, registry items, and directories. Generally, you need to specify the type of object followed by a path to that object.
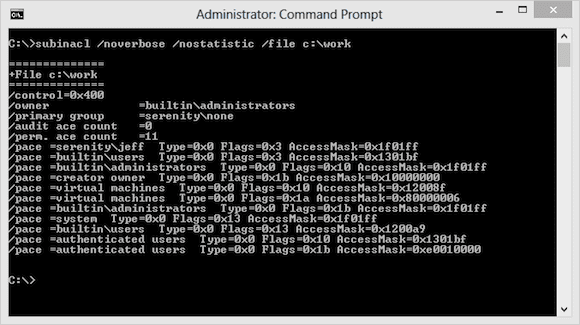
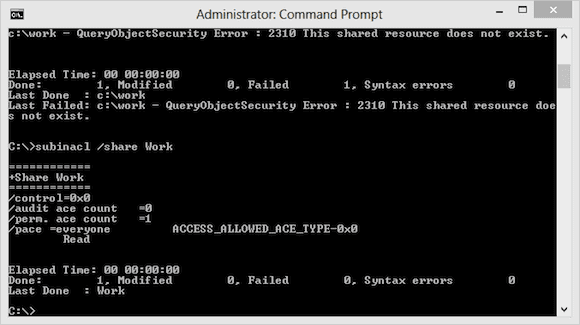
C:\>subinacl /noverbose /nostatistic /file c:\work
Even though C:\Work is a folder, I can specify it as a “file” object.
Or something like this:
C:\>subinacl /share Work
Actions
Finally, as the name implies, the action is what you want to do with or to the object. The default action is to display the current permissions, which you can see in the screenshots above. But you might want to grant, modify, or remove permissions. SubInACL has its roots in the days when domain migrations presented challenges in transferring permissions. Perhaps you still run into that issue. If so, then subinacl.exe might be the right tool.
Sample Usage
Let’s look at a sample usage. I have a share WORK where currently the Everyone group has READ access. I want to give the group CHANGE permission to the share. First, I can test my change.
C:\>subinacl /share Work /grant=Everyone=C /testmode Work : delete Perm. ACE 0 \everyone Work : new ace for \everyone Work (TestMode) : 2 change(s) Elapsed Time: 00 00:00:00 Done: 1, Modified 1, Failed 0, Syntax errors 0 Last Done : Work
This shows me that subinacl.exe wants to delete a permission and then apply a new one. The /testmode switch is like –WhatIf in PowerShell. Now to make the change for real, and I’ll have SubInACL ask me for confirmation.
C:\>subinacl /share Work /grant=Everyone=C /confirm Work : delete Perm. ACE 0 \everyone Work : new ace for \everyone 009044A8 : Continue (Yes,No) ?yes Work : 2 change(s) Elapsed Time: 00 00:00:13 Done: 1, Modified 1, Failed 0, Syntax errors 0 Last Done : Work
SubInACL can appear a bit daunting at first. But with a little patience and testing you can quickly get the hang of it. Fortunately, PowerShell in Windows 8 and Windows Server 2012 offer new tools to handle complex tasks where we might have used subinacl.exe in the past. But, if you run into a complicated permission issue, especially one you are trying to automate, subinacl.exe might be just what you need.