Semperis Hybrid Identity Protection Conference 2021
- Blog
- Hybrid Cloud
- Post

The Hybrid Identity Protection (HIP) Conference is the premier educational forum for IT pros tasked with managing identity and securing hybrid cloud environments. As the global health pandemic and move to digitalization change the way enterprises work, the HIP Conference helps IT pros to learn and implement technology that mitigates new business risks.
The conference was voted best in the 2020 and 2021 Globee Awards, and the Cyber Security Excellence Awards and IT World Awards in 2020. And although HIP has been virtual since last year, it attracts speakers from C-level executives to some of the best-known technologists in the industry.
Sponsored: Semperis is an enterprise identity protection company that enables organizations to quickly recover from devastating changes and disasters that compromise Active Directory, on-premises, and in the cloud.
What need does the Hybrid Identity Protection Conference fill
A recent report by Gartner suggests that by 2025, only 3 percent of organizations will have moved fully to using a cloud identity management solution like Azure Active Directory (AAD) for authentication. That means organizations are going to be working with hybrid cloud environments for the foreseeable future. And adding Azure AD to the already difficult task of managing on-premises Windows Server Active Directory, adds to the risks and challenges for IT departments.
The Hybrid Identity Protection Conference helps IT professionals deal with the problems of managing security in a hybrid cloud world. And it’s especially beneficial for big organizations that have a large investment in line-of-business applications that have been developed in-house. Moving on-premises applications to the cloud isn’t a simple lift-and-shift operation, so it could be years before all an organization’s applications can be reengineered for the cloud.
The move to the cloud has refocused the need to look more carefully at security as business applications are made accessible on the public Internet. The intranet firewall is no longer the network boundary; identity is the new perimeter.
The focus of the Hybrid Identity Conference
The original focus of the conference was to bring together the best industry technologists and minds with experience in Active Directory, with a goal to focus on technical subjects and without any marketing. But importantly, the conference is a place where the community can exchange ideas and experiences, bringing IT pros up to speed to deal with the new challenges of hybrid identity.
HIP has its origins in the Directory Experts conference, which Gil Kirkpatrick, Chief Architect at Semperis and Microsoft MVP, helped launched in 2001. And while there’s now a shift from on-premises AD to the cloud, the IT pros responsible for managing Windows Server Active Directory are now leading the move to hybrid identity. HIP is for IT pros who find themselves tasked with this responsibility, shedding light on technologies like OAuth, OpenID Connect, and Azure AD.
Active Directory and Azure Active Directory are at the center of hybrid identity
The Hybrid Identity Protection Conference focusses on Active Directory and Azure Active Directory because ninety percent of businesses use them for their identity needs. And because AD and AAD are so widely used, they have become a primary target for cyber criminals.
Research shows that in most breaches, Active Directory plays a role in allowing criminals to get access to corporate data and systems. And because organizations are synchronizing on-premises AD accounts to Azure AD, it’s crucial to ensure that privileged on-premises accounts don’t get accidently exposed in the cloud.
Practical steps to address the “before, during, and after” phases of an attack
The conference includes sessions to assist IT pros in preventing attacks against Active Directory, like the session Practical Tips for Protecting Active Directory, which will be hosted by Darren Mar-Elia, Semperis Vice President of Products.
And in Top 5 Risky Account Security Configurations, Alexandra Weaver (Semperis Solutions Architect) and Sean Deuby (Semperis Director of Services), will be looking at account configuration settings in Active Directory that can lead to breaches.
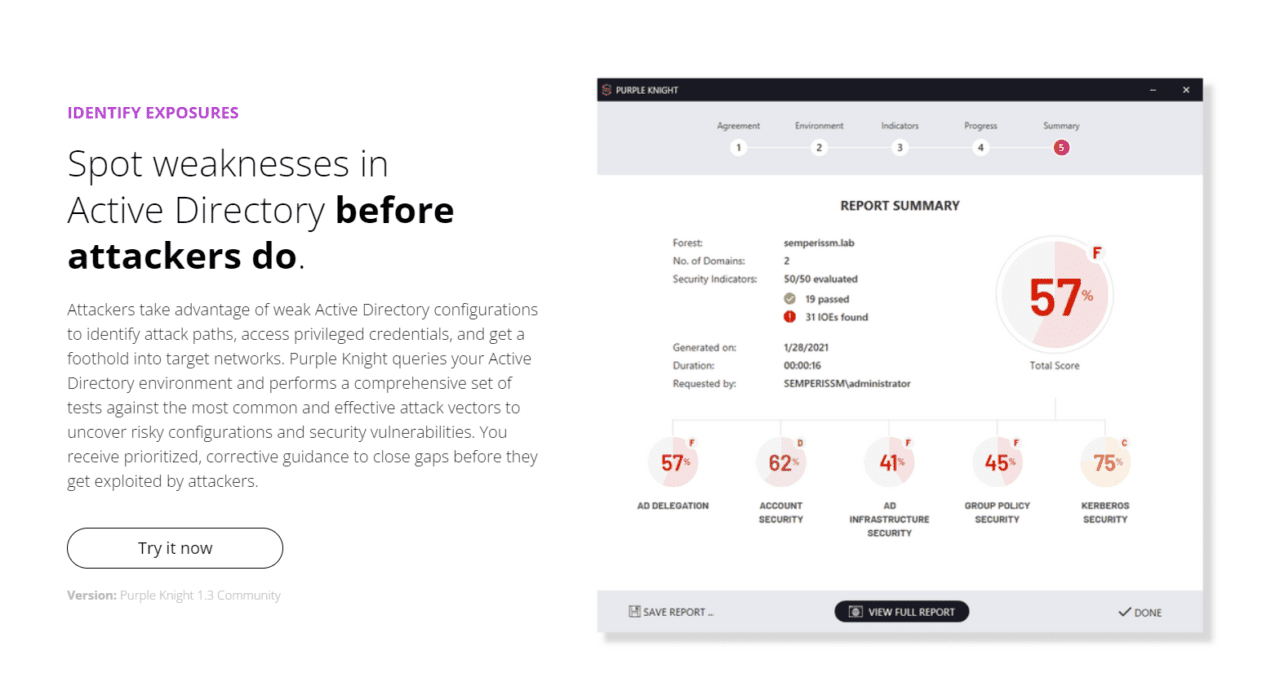
Purple Knight – Protect Active Directory against attack
Semperis has a free tool, Purple Knight, that provides a security assessment that IT can use to identify weaknesses in Active Directory configuration before attackers do, and then harden defenses. Purple Knight maps pre- and post-attack security indicators to the MITRE ATT&CK framework, providing IT with an overall risk score, the likelihood of compromise, and remediation steps.
Ran Harel, Principal Security Product Manager at Semperis, is hosting a session on the Top Legacy AD Infrastructure Vulnerabilities and How Attackers See Them. Ran will be looking at specific AD vulnerabilities, including PetitPotam and PrintNightmare, to help IT pros understand how attackers are detecting them and how you can use a tool like Purple Knight to detect them too.
Sharing knowledge about how to defend Active Directory
As criminals share information on how to attack AD and Azure AD, the HIP Conference provides a platform where IT pros can share the same knowledge. Hackers don’t break in, they log in. So, IT pros need to know how to effectively implement a least privilege security model and how to identify systems that have risky security configurations.
Organizations must be able to defend systems against attackers that have already gained an identity that they can use to log in. Once an attacker has gained a foothold in AD, even as a standard user, it might be possible for them to elevate privileges and take ownership of business data and infrastructure.
Recovering Active Directory
Most organizations aren’t well prepared to recover their Active Directory environments. And because of the scale and complexity of today’s cyberattacks, in the event of a breach, organizations need to be prepared to start from scratch when restoring their environments.
Even if an organization is prepared, the recovery process is complicated. To help IT pros navigate the disaster recovery process, Jorge De Almeida Pinto (Lead Identity/ Security Consultant IAMTEC), has a session where he will show IT pros how automate the recovery process using PowerShell.
What are verifiable credentials?
John Craddock’s session, Will Decentralized Identities and Verifiable Credentials Become the Future of Identity?, introduces IT pros to the concept of verifiable credentials and how to issue your own using the Azure AD Verifiable Credentials service. Verifiable credentials are decentralized credentials that are not stored in a central repository, like the Active Directory database, but instead installed on a blockchain. This allows users to authenticate to their verifiable credentials and pass them on to third parties. Much like in the physical world, where you might present a passport or driver’s license to verify certain claims.
Verifiable credentials bring advantages for users and businesses alike. For example, if an identity provider like Active Directory or a public provider like Facebook go down, then organizations that rely on them for user authentication are not able to do business. Decentralized credentials can help solve this problem.
FIDO2 and passwordless authentication
FIDO2 is the leading standard in passwordless authentication. And passwordless technology, like Windows Hello, is based on it. But moving users to passwordless authentication, especially for large organizations, isn’t a simple process.
Joe Kaplan, Senior Manager of Technology Security at Accenture, will be delivering a session called Taking a Large Organization Passwordless: Completing the Journey. His session will help IT pros and organizations plan for passwordless authentication, including addressing business problems like getting leadership buy-in.
Behavioral authentication
Jim Routh – board member, advisor, former CISO of Mass Mutual, CVS and Aetna Advisor – has a keynote called Why We Need Behavioral-Based Authentication Solutions, which details why organizations need behavioral authentication to eliminate account takeover and reduce operating costs. Jim will also provide practical considerations for implementing behavioral authentication and give some real-world examples.
Security and identity teams working together
Surveys and research have shown that there is a disconnect between the people who implement security and identity. To address this issue, some organizations are changing their structure so that the security and identity teams can work more closely together.
Organizations often see AD as an infrastructure service, but it’s not always considered a system that’s important for security. Identity and security teams must work better together to solve the challenges of hybrid identity protection, making it a core component of an organization’s security posture.
What the future holds for the Hybrid Identity Protection Conference
Because sophisticated attacks can now be launched by unsophisticated attackers, the challenge of protecting data and systems is considerable. The HIP Conference aims to provide IT pros with the knowledge and expertise they need to understand how they can protect against attack and close holes in their infrastructure that could lead to compromise.
Because large-scale adoption of technologies like passwordless and behavioral authentication are some years away, the near future is going to see more of the same as organizations and hackers engage in a cat and mouse game where criminals develop new attacks and organizations attempt to shut them down.
The next few years will see the HIP conference continue to provide IT pros with what they need to address the following issues:
- Secure your environment to prevent attacks
- Monitor your systems to detect intrusion
- Respond to security breaches
- Recover from breaches
There will also continue to be an emphasis on providing information on how organizations can implement basic best practices to secure their environments. Experts will share information on the best practices that should be implemented in both AD and Azure AD, keeping attendees up to date on how those best practices are evolving to help reduce the risks for businesses.
You can find more information about the Hybrid Identity Protection Conference, which runs December 1st to 2nd, 2021, including a list of all the sessions, speakers, and keynotes, on the conference website. Along with a link to registration, which is now open.