Microsoft Introduces AES-XTS to BitLocker in Windows 10 Version 1511

In today’s Ask the Admin, I’ll explain changes to BitLocker full disk encryption made in Windows 10 Version 1511.
You’re probably already familiar with Microsoft’s full disk encryption technology, first built-in to Windows 7 and Windows Server 2008 R2. While BitLocker is a convenient way for consumers and organizations to manage full disk encryption in Windows, it hasn’t been without its critics. Much hangs on whether you trust Microsoft, because BitLocker is not open source, so the source code can’t be checked for backdoors.
In 2008, researchers discovered that BitLocker is vulnerable to ‘cold boot attacks,’ where the contents of pre-boot memory can be read from DRAM up to several minutes after a device has been powered off — although Linux, OS X and other OS full disk encryption technologies are also susceptible to this form of attack.
Physical access to a device is required to perform a cold boot attack, although the risks can be reduced by using a Trusted Platform Module (TPM) and PIN. On the plus side, Windows better protects the boot process than other OSes, preventing attackers from running modified boot code.
No More Elephant
AES in Cipher Block Chaining (CBC) mode was the algorithm of choice in Windows 7 and Vista, and Microsoft added a diffuser to provide ‘some additional security properties that are desirable in the disk encryption setting but which are not provided by AES-CBC cipher methods.’
But in Windows 8, Microsoft changed the default encryption options and completely removed the ability to use the aes128_Diffuser and aes256_Diffuser – Elephant Diffuser – options. Microsoft cited speed and non-compliance with encryption standards as the primary reasons for removing the Elephant Diffuser, although the code was retained to ensure backwards compatibility with drives encrypted in Windows 7.
AES-CBC provides something that’s known as poor man’s authentication, which makes the assumption that manipulated ciphertext when decrypted won’t result in meaningful plaintext, hopefully resulting in an operating system crash and thus preventing a hacker from performing evil deeds.
Microsoft goes on to say: ‘The only task of the diffuser is to make manipulation attacks harder by providing better poor-man’s authentication than plain AES-CBC provides. Given the limited BitLocker attack model we consider it extremely unlikely that a practical attack against the diffuser will be found.’
Without a diffuser, knowing the location of files on disk could allow an attacker to modify specific files. With a diffuser in place, an attacker could still change the encrypted bits, but the decrypted files would more likely result in corrupted files that cause the OS to crash.
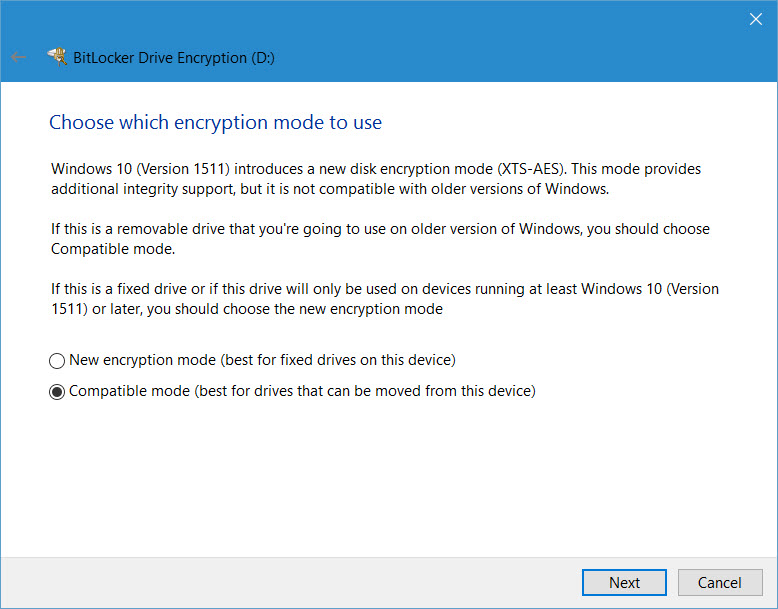
Microsoft Compromises on AES-XTS
When Microsoft designed BitLocker, AES-XTS was relatively new, and assumedly as an unproven solution was not considered for that reason. But in Windows 10 Version 1511, AES-XTS is now the standard encryption algorithm, and while it provides less diffusion than AES-CBS + Elephant, it is an accepted standard and works faster than AES-CBS + Elephant.
AES-XTS is not perfect, but then full disk encryption is not easy, and there’s no perfect solution at present that provides the balance of performance and security that might be considered desirable. All we can hope for is that in the future Microsoft, or someone else, develops an encryption standard that meets all the requirements of modern computing. But in the meantime, AES-XTS provides a reasonable solution that’s not only used in BitLocker, but also other popular encryption products.



