This article is the fifth and last in the series “What is Microsoft Mobility Suite?” These days, we can’t stop talking about cyber threats, hacking and data breaches to the enterprise. How much data has corporation X admitted to have lost or negligently disregarded? These are all valid concerns that should not be taken lightly, and oversimplifying this issue is making a great disservice to the public.
What is Microsoft Advanced Threat Analytics?
It is the public’s data we are talking about, and it’s this group that ends up suffering for the negligence of many, many corporations. Responsible enterprises protect data by having a set of services that prevent intrusions and data breaches. Microsoft Enterprise Mobility Suite includes the Microsoft Advanced Threat Analytics service. This article will cover what Advanced Threat Analytics is and how it works. This service is one of the best solutions to overly complicated and expensive alternatives. By leveraging the power Azure and their other cloud services, Microsoft’s Advanced Threat Analytics offers a wide range of integrated solutions that help analyze behavior, detect malicious attacks and search for known threats with the common goal of preventing data breaches by reducing the size of breach vectors.
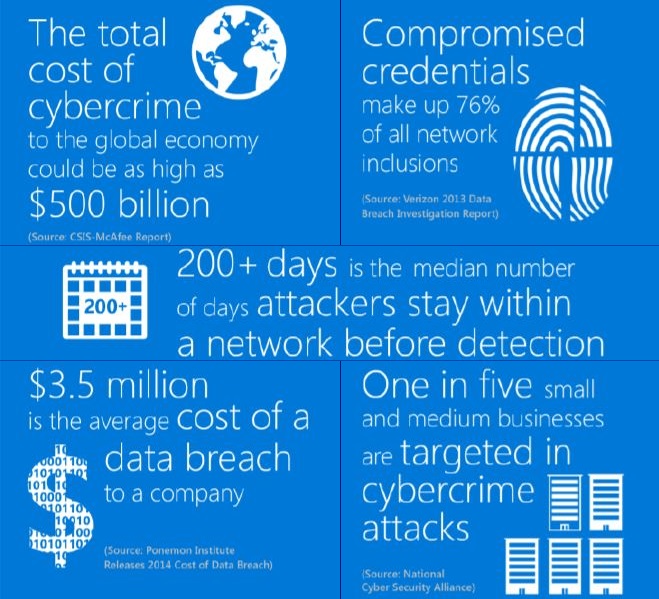
Today’s world shows us a harsh reality: Threats and attacks have grown and become increasingly more complex, more sophisticated and more frequent. Customer privacy, brand recognition, public relationships and even executives’ reputation are at stake every time there is a new breach. It is up to the enterprise to choose wisely from the many solutions available to prevent these attacks. Information and analysis of such attacks (that sometimes cannot be fully prevented but mitigated) help a new generation of services build onto their existing security patterns. The average number of days an attacker stays completely undetected in the network accessing data is more than 200 days. More than 76 percent of all network intrusions are traced back to compromised credentials. The average cost of a data breach to a company is $3.5 million. The global cost of cybercrime to economies is $500 billion.
With Advanced Threat Analytics, Microsoft has built a set of services that helps detect threats faster and reduces the time a threat can be active before detection. Microsoft Advanced Threat Analytics can adapt as fast as the cyberthreats do. By learning common organizational patterns from the enterprise, Advanced Threat Analytics is more adept at determining whether a transaction was legitimate or not. If the business and its rules change, Advanced Threat Analytics learns how to change from those changing patterns.
Using a simple attack timeline to show and focus on what is important, an overwhelming volume of data is set aside for deeper research after the fact while the immediate set of information is reported in a concise manner. Things like the who, what, when and how are set in perspective in these useful reports with an option to dig deeper if necessary. At the same time, the service also provides recommendations for further investigation and remediation tasks for each set of suspicious activity.
One of the unwanted effects that most threat prevention packages have is that they flood inboxes with notifications. These mostly false-positive alerts create what is called “false-positive fatigue” or the illusion that everything seems to be a false alarm while everything seems to be fine and nothing of significance is going on and thus give a false sense of security. Microsoft Advanced Threat Analytics reduces notifications to exception-only. When these exception alerts are sent out, they can be handled with the proper sense of urgency that they require and a catastrophe can be avoided.
How Does Advanced Threat Analytics Work?
The inner workings of Advanced Threat Analytics can be broken down into four main steps: Analyze, learn, detect and alert. Advanced Thread Analytics can be integrated with both Active Directory on-prem and Azure Active Directory, described in an earlier article in this series, along with other relevant components.
Analyze. The first step is to analyze current and existing services inside the organization. Microsoft Advanced Threat Analytics relies on deep packet inspection, Active Directory traffic, and diverse sets of information for analysis.
Learn. The second step for Advanced Threat Analytics is to learn and profile behaviors of users, devices and resources. This is akin to a security specialist understanding what each individual does to get a baseline of what is considered normal usage. This information is used as a feed into Advanced Threat Analytics learning technology to build what Microsoft calls an Organizational Security Graph or a map of entity interactions that represent the activities between each user, device and resource and the context in which they happen.
Detect. The third step in Advanced Threat Analytics is to detect any anomalies or interactions in that map that look out of place. The kind of which could be compared to an investigator’s hunch. Given enough of these detected anomalies, red flags can be raised that can be combined or kept separate from detection of known attacks or known security intrusion events. Some of these can be broken trusts, the use of weak protocols, known protocol vulnerabilities.
Malicious attacks can be detected by knowing when pass the ticket, pass the hash, forget PAC, reconnaissance or brute force attacks are happening and having them flagged. Abnormal behavior can also include anomalous logins, unknown threats, password sharing, lateral movement, etc. These are only some of the detection targets for Advanced Threat Analytics, which will be complemented with adaptive logical questions that will have to be answered to adjust the detection process to the particular intricacies of the organization where it is installed.
Alert. Finally, the fourth step is to alert appropriately and in a measured way that includes not only the security issues affected, but also actionable suggestions on what to correct and how to prevent it next time. Alerts include information by also providing the simple attack timeline tool.
Find Threats Faster with Advanced Thread Analytics
While this is just an overview of Advanced Threat Analytics, hopefully you will be able to see how complete this tool really is and when used in combination with the rest of the components in Microsoft Enterprise Mobility Suite, you will see the value proposition that it will bring to your organization. Even if you have a set of similarly featured services, none of them will integrate as well or as tightly as these solutions do with each other as part of the Enterprise Mobility Suite.



