
In today’s Ask the Admin, I’ll explain what Windows Hello for Business is and how it differs from Windows Hello for consumers.
Nobody likes passwords. Users don’t like them, IT dislikes them even more, and most importantly, they’re an insecure relic from the past that we still rely on every day. But Microsoft is attempting to banish them to the great technology trash can in the sky. Passwords are bad for many reasons, not least because they can be guessed, recycled across different sites — making it easier for hackers to gain entry to multiple systems — exposed in server breaches, and can be used in replay attacks. Social engineering can also lead to users unwittingly handing over their credentials to the bad guys.
Windows Hello
To put an end to this security quagmire, Microsoft introduced Windows Hello in Windows 10. Instead of entering a password to sign in to Windows, users can set up a gesture: either a PIN or biometric authentication method. If your device doesn’t support biometric authentication, Microsoft recommends using a PIN that’s unique to the device instead of signing in with a common password, to reduce the risk of your password being compromised. If the PIN gets compromised, then the hacker can gain access only to the device, and not your Microsoft account, as the PIN cannot be used to access your account from any other device.
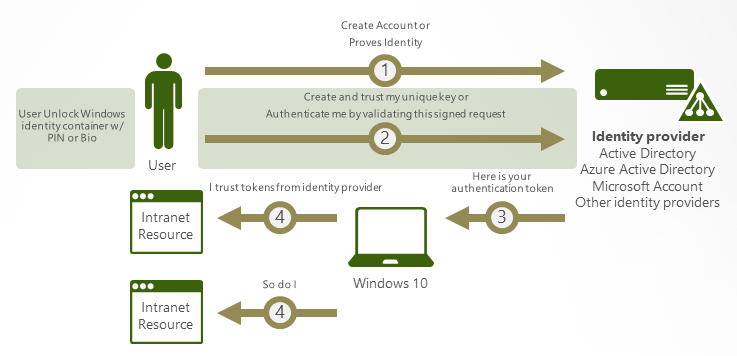
Enrollment is a two-step verification process that establishes a trust relationship between an identity provider, such as Azure Active Directory (Azure AD), and a user account; from which point users only need to provide the gesture to sign in. Windows Hello supports the following types of account:
- Microsoft accounts
- Active Directory (AD) accounts
- Azure AD accounts
- Identity providers supporting Fast ID Online (FIDO) v2.0 authentication
Instead of relying on shared secrets, Hello replaces passwords by creating a cryptographic key pair in a Trust Platform Module (TPM) if present, or in a software-based container. When a PIN or gesture is used to log in, the trusted identity provider issues an authentication token to the user if the keys and gesture are a verified identity. Attestation is used to prove to the identity provider that the keys are bound to a TPM, and if not, the identity provider assumes the Windows Hello key is created in software.
Windows Hello for Business
At the initial launch of Windows 10, Windows Hello for Business was two separate technologies: Microsoft Passport for Work and Windows Hello. But to simplify deployment, the two products have been merged into one: Windows Hello for Business.
In addition to what I’ve already described, Windows Hello for Business adds support for certificate-based authentication, and can be managed by Group Policy or Mobile Device Management (MDM) policy. It’s worth noting that AD accounts cannot be backed by key-based or certificate-based authentication, although Microsoft is planning to add support in the future.
Windows Hello provides two-factor authentication, with one factor being the key or certificate that’s bound to the device, and the second a gesture, such as a PIN or biometric authentication. Gestures are stored locally on devices and never roam. Enterprises that have a Public Key Infrastructure (PKI) in place can use certificate-based authentication with Hello, but hardware-based keys generated by TPMs provide the most secure solution if the hardware is available to support it, and doesn’t require PKI.
In a forthcoming article on the Petri IT Knowledgebase, I’ll show you how to set up Windows Hello for Business.
Related Article:


