How to Achieve World-Class Windows Patching Like a Pro
One of the most difficult and rewarding topics on an IT Pro’s plate – Patching. If you’re an IT Pro responsible for patch management in your organization, are you following the right approach to achieve world-renowned status on doing it effectively? Let’s take a look at some methods and procedures to get you that next award and recognition.
On the second Tuesday of the month – “Patch Tuesday” – Microsoft releases the latest security update rollups for all Windows clients and servers. This is their “B” release (week 2). Over the last few years, Microsoft has heard from you IT Pros and other chief information security officers that you’ve placed greater attention on patching and take a more liberal stance on getting devices patched and secured ASAP. The is explained by the fact that the adoption of formal patching policies is on the rise. This post will also describe how to dramatically enhance your company’s patching policies with the least impact on your users. The key – a ‘cloud cadence’ mindset. Hold that thought for a moment.
Fundamentally, there are two key transformative changes you can make in your organization that will boost the efficiency of update management:
- Streamline your review and approval process. This is the ‘cloud cadence’ mindset. This is crucial to how fast your devices get patched and compliant. The key value-add here is getting your devices protected BEFORE exploits appear in the wild and on your users’ devices! Proactive vs. reactive.
- Tune the efficiency of the update machinery. Windows Update includes many policies giving you granular administrator control over your devices for specific situations. However, this can have a detrimental effect on how often patches are installed, the prevention of patches altogether, or an even worse end-user experience. (Wait, WHY did my computer reboot overnight!?)
Why effective monthly patching matters
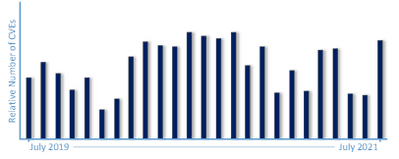
Because bad actors can exploit insecure environments at ever-increasing rates, we are forced to be more diligent about deploying service updates as soon as possible. Over time, the numbers of common vulnerabilities and exposures (CVEs) are going up. Each open vulnerability is another attack vector in your environment.
A classic double-edged sword – while it’s always helpful that Microsoft releases security patches on a general, known cadence (“B”, “C”, etc), it can supply the bad actors out there JUST what they need – ammunition to reverse engineer fixes to learn how to exploit them!
Adopting cloud-based monthly patching strategies
Depending on your organization’s size and how many regulatory requirements are imposed on you, you may already be working to reduce the time required to hit a specific monthly update threshold. Organizations that rebuild their update process can achieve world-class adoption each month using endpoint management tools. Tools like Microsoft Endpoint Manager and Microsoft Intune are the recommended tools for medium to large enterprises. If you don’t have the resources/time to devote specific expertise to update management, it may behoove you to adopt a cloud-managed distribution model for monthly updates using Microsoft Intune or co-management.
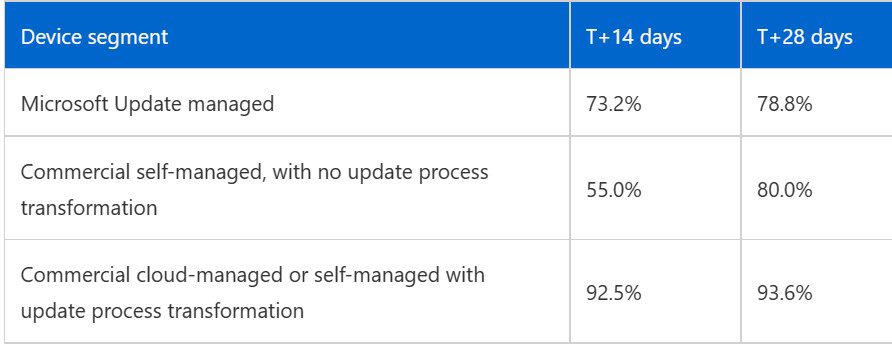
Let’s define three segments and compare adoption results:
- Microsoft Update managed. These are devices connected to the Windows Update service but are not configured with any administrative policies. The local Windows Update service assumes the entire role of getting patched. This is most consumer devices – Consisting of irregular schedules, offline issues, and are difficult to update on any schedule.
- Commercial self-managed, with no update process transformation. This group of devices is managed by IT Pros using on-premises infrastructure based on more traditional tools like Windows Software Update Services (WSUS), but policies are not configured with Microsoft’s magic ‘cloud-cadence’ mindset (shame…)
- Commercial cloud-managed or self-managed with update process transformation. These devices win the prize. These are managed with Microsoft Endpoint Configuration Manager or Microsoft Intune (backed by Windows Update for Business), where specific update policies are configured with the ‘cloud cadence’ wizardry…eh, ‘mindset.’
Here are the average adoption rates among these three segments with data from December 2000 through February 2021.
Obviously, achieving a > 90% adoption rate is stellar! This shows you the power and efficiency of the commercial, cloud-managed methods. Adopting the ‘cloud cadence’ philosophy fundamentally will help you accomplish these awesome results. Another aspect you need to eliminate is more traditional, often-misunderstood policies around the tuning of update behaviors. These can result in slowing down the update schedules. This causes detriment to both the speed of patches and the user experience. Finding that happy equilibrium, or balance between getting the job done and NOT ticking off your users can be delicate. But, in times like these, let’s get a tad more stringent, OK?
Streamline your review and approval process
The number of vulnerabilities is increasing across all software, not just the operating system. You must take a proactive approach by accelerating how quickly you protect your devices. It is best to adopt strategies and processes that allow for more rapid deployment of monthly servicing patches safely.
The first, most vital thing you should do is to reimagine how you review and approve monthly servicing updates. Microsoft calls this adopting a..wait for it… “cloud-cadence” mindset. 🙂 This is less about technology and more about making a cultural shift away from legacy deployment approaches to service management maturity. So, what does a cloud cadence mindset really mean?
Here’s a good analogy. The introduction of the production assembly line more than a hundred years ago helped achieve the completion of a ‘single item’ to be produced in a fraction of the time, compared to one at a time. The actual steps don’t fundamentally change between the two methods, but the efficiencies are hard to ignore! The same transformation can be achieved when managing updates in your organization. You can treat each update—let’s say a car, for example—as a project that must be fully reviewed, approved, and deployed as a single project before moving on to the next project. Or, for greater efficiency, you can adopt an approach where updates are constantly flowing. If you detect an issue, hit the “pause” button on your assembly line to diagnose and remediate the issue. Once remediated and you have high confidence that the issue has been addressed, you then resume the deployment process.
Microsoft has adopted the concept of ‘rings’. With the Windows Insider Program (WIP) for example, they first created the Fast ring, the Slow ring, etc. Last year, they migrated to today’s list – the Dev channel, the Beta channel, the Release Preview channel, etc. Dividing devices in your organization into groups, you order them from highest to lowest tolerance for issues. You steadily progress through these rings, carefully watching signals received should a pause be necessary. Microsoft has received feedback from IT Pros that this approach saves their organization a lot of money. The key to the success of this approach is to build and maintain highly effective listening mechanisms to surface any anomalies quickly, minimizing the impact of those anomalies on the rest of the update ring.
To learn more about how to develop your ‘update rings’, check out this MS Ignite session!
Tune the efficiency of the update machinery
Here are three top factors to consider for monthly device updates:
- Is the device active and connected? – Does it successfully contact its update control point to learn of the update, and is it connected long enough to download and process the update?
- Is the device properly configured? – Is the device impeded to learn about and install new patches?
- Has a deadline policy been set? – After connectivity, this is the most important consideration.
Microsoft consistently finds these three factors to contribute to slower update adoption rates amongst self-managed commercial organizations. They recommend leveraging the cloud via the Windows Update for Business service to download and update monthly patches to devices. Utilizing MECM and Intune, if a device has an internet connection, it will be notified of updates and download them from a Windows Update distribution point.
The device update has four phases:
- Scan. A device checks Windows Update or your WSUS server for updates at scheduled intervals. Each update is evaluated against organization policies (MDM or Group Policy).
- Download. Once the device determines an update is available, it downloads it.
- Install. After downloading, depending on the device’s Windows Update settings, it will be installed in the background, with no end-user impact.
- Commit and restart. Once installed, the device will usually require a restart to complete installation.
The first three phases happen in the background with no visible end-user interruptions. You can get more details on the policy and settings configurable here in the Windows 10 Update Baseline. By utilizing cloud-based updates and using recommended optimizations, Microsoft sees significantly better deployment of updates at organizations. This also includes employees of Microsoft, where Microsoft IT transitioned from traditional on-premises update management to cloud-delivered optimized delivery.
Conclusion
Microsoft urges customers to engage the ‘cloud cadence’ mindset if they’re struggling to achieve monthly servicing goals in their IT departments. Moving to the cloud-delivered methodology can get you great results just two weeks after Patch Tuesday.
To learn more about how Microsoft IT transitioned as described above, read this white paper. Also, there are some good Ignite sessions to browse: