Guide: Getting Started with Zero Trust Security in Microsoft 365
Zero Trust is a security model that can be applied to Microsoft 365. It focuses on improving security by verifying and testing both the identity and device before granting access to resources. You can think of Zero Trust as a way of working, wherein you take it for granted that every user and device accessing your environment – in or out the network – to be compromised, and hence, take actions to confirm the validity of each of those.
In these times when the usage of devices, applications to access internal resources from different locations has increased due to the pandemic situation, securing yourself from threats through aggressive and proactive policies is important.
This is the first article in the Microsoft 365 Zero Trust series. Here, you will be introduced to the various concepts of Zero Trust in Microsoft 365, along with several pieces of information to help you to gain an adequate level of understanding of this security model.
The Principles
Zero trust follows the idea of “never trust, always verify”. Microsoft has defined 3 principles on which zero trust operates:
- Verify Explicitly: Every point like user identity, location, device state, and health must be taken into consideration before granting anyone access to resources. The emphasis is on always authenticating and then authorizing based on the points mentioned here.
- Use Least Privileged Access: Admin roles must be granted with limitations like just-in-time and just-enough-access strategy.
- Assume Breach: Security experts must assume that resources are breached and take measures to limit the damage. Use of analytics to detect threats and harden security is important.
The Pillars of Zero Trust in Microsoft 365
- Strong Authentication: Every identity requesting access must have strong authentication enabled. Multifactor authentication ensures that all identities are protected with an additional layer of authentication. You may refer to this link to read more about multifactor authentication.
- Ensure access is compliant and typical for that identity: The identity must not be compromised or flagged for risky sign-ins.
- Least Privilege Access: Identities must be provided with access only to those resources which are required for their tasks. This reduces the chances of unwanted actions in the environment.
There are a few aspects of the environment that need to be set up before deploying zero trust in identity.
- Cloud identity federates with on-premises identity systems – If you run an on-premises AD, then this must be connected to Azure AD.
- Establish your Identity Foundation with Azure AD – Azure AD should be the decision-maker as far as providing access to users is concerned. All-access requests must traverse through Azure AD.
- Integrate all your applications with Azure AD – Either via configuring single-sign-on to third-party SaaS services or by publishing on-premises applications through solutions like Azure AD Application proxy.
- Verify explicitly with strong authentication – Multifactor authentication must be deployed. Legacy authentication should be blocked in the organization.
Besides these, usage of conditional access policies to manage access requests are essential, and advanced functionality such as Privileged Identity Management for identity governance and passwordless authentication are recommended. Both Microsoft Cloud App Security and Microsoft Defender for Identity help to identify risks and to contain them; hence, if you have these available, it’s recommended to configure and enable them.
Endpoints
Securing the different endpoints in Microsoft 365 is a necessary task. End-users may use different devices to connect to your organizations and access internal data; these could be your own corporate devices or personal ones. The Zero Trust mindset of verifying everything applies to endpoints too, irrespective of their type. The devices on which it’s applicable are PCs, mobiles, Apple Mac devices, tablets, and IoT devices. The device will be verified even if they are within the corporate network.
There are again some base rules in zero-trust for endpoint security. The security policies are to be set up in the cloud and centrally enforced. They should include endpoint security, device configuration, app protection, and device compliance. The device platform and apps running on it must be verified and updated.
Security compromises can be dealt with automated responses to limit access to resources. Also, a centralized access control system means the policies are already applied on the data before they are accessed.
In order to deploy zero trust security in endpoints, you must fulfill certain pre-requisites:
All the endpoint devices must be registered with a cloud identity provider like Azure – This inventory makes it easy to apply the restrictions.
DLP policies must be enforced on all the devices – Once access is provided to a resource, you must ensure that restrictions are applied on the actions that the identity can perform on the resource.
Endpoint Threat Protection must be enabled – A centralized portal to detect and action risks. Endpoint logs can be routed to SIEM and PowerBI using Intune Data warehouse.
Access control is gated on endpoint risk for both corporate devices and BYOD – The severity of the risk associated with a device will decide the level of access provided to it over the resources. The security analysis of ATP is used to create policies to achieve this goal.
Applications
- Gain visibility into the activities and data in your applications by connecting them via APIs – Here, you must use cloud app security to monitor the activities of the applications and take actions using the application APIs.
- Restricting Shadow IT usage – Usage of unapproved applications in an organization can create a risky situation. You can utilize Cloud Discovery along with Microsoft Cloud App Security to monitor the traffic logs and analyze them. Analyzing the traffic logs against a list of approved applications will show you the undesired apps.
- Protect sensitive information and activities automatically by implementing policies – Using cloud app security you can define policies like anomaly detection, access related, file policy, and session policies to control the actions of your users.
- Deploy adaptive access and session controls for all apps – Least privileged access and rigorous verification are the guiding principles of Zero Trust security. The same is applied here on the level of access provided to applications over resources. You must use Cloud App Security Conditional Access Policies to monitor and control apps.
- Strengthen protections against cyber threats and rogue apps – To protect yourself against malicious applications, you must use Cloud App Security and its related tools like user and entity behavioral analytics (UEBA), anomaly detection, impossible geographical travel, ransomware, suspicious inbox rules among others.
- Assess the security posture of your cloud environments – Use Cloud App Security to monitor and assess the risks across your cloud infrastructure
Data
Data is a valuable commodity. It traverses through all the areas of the environment like networks, endpoints, apps, and infrastructure. The data protection strategy in Zero Trust Security is:
- Know your data.
- Prevent data loss
- Protect your data
- Govern your data
Let take a brief look at the deployment approach for Zero Trust Security for Data:
- Access decisions are governed by encryption – Sensitive data must be encrypted to secure it in every stage. Sensitivity labels can be used to classify them.
- Data is automatically classified and labeled – Azure Information Protection can be used to achieve this. You can also configure auto-labeling for Office apps and apply sensitivity labels automatically.
- Classification is augmented by smart machine learning models – You can leverage machine learning capabilities to label massive amounts of data. At present this can be done manually, or by using automated pattern matching and also via the trainable classifiers method.
- Access decisions are governed by a cloud security policy engine – Cloud app security can be used to govern the sensitivity labels.
- Prevent data leakage through DLP policies based on a sensitivity label and content inspection – DLP policies should be used to identify and protect sensitive data across Microsoft 365.
Infrastructure
Securing the infrastructure is another critical requirement for any environment. IT infrastructure is categorized as hardware, software, network infrastructure among others. These can be either on-premises or in the cloud.
Networks
The zero trust principle of testing and verifying every identity and endpoint even if it’s within the network is applied here too. The approach is to pre-empt attacks and prepare for them.
Deploying Zero Trust Security in Networks involves the following points in brief:
- Network segmentation: Many ingress/egress cloud micro-perimeters with some micro-segmentation – This method uses different segments for each workload. Every segment has its own ingress and egress traffic controls thereby ensuring that its bandwidth is not abused by unauthorized access. This removes the dependency of having a single pipe in the network.
- Threat protection: Cloud-native filtering and protection for known threats – Applications in the cloud that have connections with external environments or with on-premises need to be monitored for threats originating from those areas. Traffic from these can be scanned using Azure Web Application Firewall. You can also setup rules for such traffic using Azure Front Door and Azure Application.
- Encryption: User-to-app internal traffic is encrypted – The user-to-app internal traffic must be encrypted.
- Network segmentation: Fully distributed ingress/egress cloud micro-perimeters and deeper micro-segmentation – The network components can be further segregated. Now you should segment it into different subnets using virtual network subnets and network security groups rules.
- Threat protection: Machine learning-based threat protection and filtering with context-based signals – Azure DDOS Standard Protection should be enabled to monitor your Azure traffic. It uses Machine learning techniques to detect traffic loads and to take mitigation actions.
- Encryption: All traffic is encrypted – Encryption of traffic will boost security.
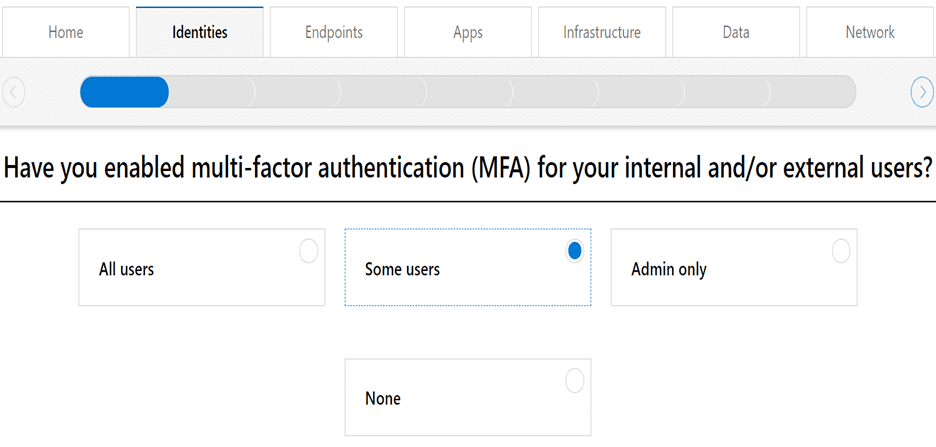
Zero Trust Assessment Tool
This tool poses some questions about your organization’s setup and then provides feedback on the basis of those. You can take a different assessment for each of these Identity, Endpoint, Data, Applications, Networks, and Infrastructure.
Conclusion
Most of the security measures talked about in this article would already be in use in a majority of organizations. The Zero Trust security model provides a plan of action to combine all your splintered efforts into an organization-wide template. Teams that are working in silos on these security aspects can be taken on board via this security model.
In the next post, we will explore how Zero Trust Security for Identity can be deployed effectively.
Related Article: