Expert Tech Insights: Unleashing the Power of Windows, Microsoft 365, and Microsoft Azure
-
5 Ways to Get Things Done More Efficiently in Microsoft 365
Last Update: May 07, 2024
- Apr 22, 2024
-
-
What is Single Sign-On (SSO): Everything You Need to Know
When it comes to cloud services and security technology, IT and systems administrators should seriously consider having SSO implemented for greater convenience and security. What is single sign-on (SSO)? SSO is an authentication method that allows users to securely access multiple SaaS (Software-as-a-Service) applications, websites, and other digital resources with a single set of login…
May 13, 2024 -
The Ultimate Guide to Web Application Firewalls (WAF)
An often-overlooked element of security is the Web Application Firewall (WAF), especially in cloud computing. In this article, I explain what a WAF does, the different kinds of WAF, and I discuss why you should deploy one or more WAFs in your architecture. What is a Web Application Firewall (WAF)? A Web Application Firewall, often…
Last Update: May 10, 2024
Jun 20, 2023 -
The Role of Identity Threat and Detection Response in Zero Trust Security
I recently spoke to Sean Deuby, who is Principal Technologist at Semperis and an Identity expert. Sean told me about the importance of protecting identities in the current landscape and how Identity Threat Detection and Response (ITDR) is a critical component of the Zero Trust security model. The emergence of cloud computing and the shift…
Last Update: May 10, 2024
Jun 16, 2023 -
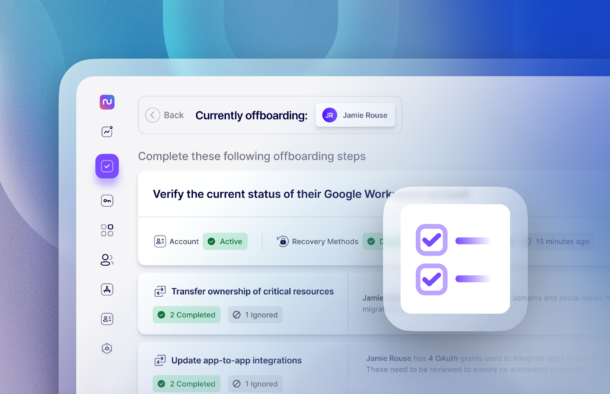
The Dirty Truth About IT Offboarding Automation
Every system administrator dreams of building the perfect Rube Goldberg machine of IT automation to manage the employee IT lifecycle, end to end, including IT offboarding. A new hire joins the company, HR files a ticket, and BAM! In an instant, all of the birthright accounts, access, and permissions are granted in a glorious cascade…
Last Update: May 10, 2024
Jul 21, 2023 -
Using Stellar Repair for Outlook to Recover a Corrupted PST
This post was Sponsored by Stellar Repair, you can learn more about their PST Recovery Tool here. Email is the de facto standard for today’s business communications. Businesses rely on email for personal communications, team assignments, announcements, and notifications as well as purchasing and other intracompany communications. This has been particularly true during the recent…
Last Update: May 10, 2024
Apr 7, 2021 -
Understanding Microsoft 365 Data, What is and Is Not Your Responsibility
When people talk about the security of data in Microsoft 365, invariably phrase you’ll hear – and I don’t know who coined it – “the cloud is just someone else’s computer”. When someone says it to me, I literally have to stop myself from saying “…but actually” before we both explode into memes. Microsoft 365…
Last Update: May 10, 2024
Apr 1, 2021
Thank you to our petri.com site sponsors
Our sponsor help us keep our knowledge base free.
Petri Experts Spotlight
-
-
Laurent Giret Editorial Manager
-
Russell Smith Editorial Director
-
Michael Reinders Petri Contributor
-
-
Michael Otey Petri Contributor
- Install and Use SQL Server Report Builder Apr 10, 2024
- SQL Server Essentials: What Is a Relational Database? Mar 12, 2024
-
Stephen Rose Chief Technology Strategist
- UnplugIT Episode 2 – In The Loop Jun 13, 2023
- Unplugging What’s Next for Teams 2.0 May 30, 2023
-
Sukesh Mudrakola Petri Contributor
-
Shane Young Petri Contributor
-
-
-
Chester Avey Petri Contributor
-
Flo Fox Petri Contributor
-
Sander Berkouwer Petri Contributor
-
Sagar Petri Contributor
- How to Create a Dockerfile Step by Step Nov 14, 2023
- What is Amazon Kinesis Data Firehose? Jul 14, 2023
-
-
-
Bill Kindle Petri Contributor
-
Johan Arwidmark Petri Contributor
- Upgrade to Windows 11 – The Road Ahead Nov 28, 2023
Sponsored Articles List
-
The Ultimate Guide to Web Application Firewalls (WAF)
An often-overlooked element of security is the Web Application Firewall (WAF), especially in cloud computing. In this article, I explain what a WAF does, the different kinds of WAF, and I discuss why you should deploy one or more WAFs in your architecture. What is a Web Application Firewall (WAF)? A Web Application Firewall, often…
Last Update: May 10, 2024
Jun 20, 2023 -
Active Directory
The Role of Identity Threat and Detection Response in Zero Trust Security
I recently spoke to Sean Deuby, who is Principal Technologist at Semperis and an Identity expert. Sean told me about the importance of protecting identities in the current landscape and how Identity Threat Detection and Response (ITDR) is a critical component of the Zero Trust security model. The emergence of cloud computing and the shift…
Last Update: May 10, 2024
Jun 16, 2023 -
Cloud Computing
Security
The Dirty Truth About IT Offboarding Automation
Every system administrator dreams of building the perfect Rube Goldberg machine of IT automation to manage the employee IT lifecycle, end to end, including IT offboarding. A new hire joins the company, HR files a ticket, and BAM! In an instant, all of the birthright accounts, access, and permissions are granted in a glorious cascade…
Last Update: May 10, 2024
Jul 21, 2023 -
Microsoft 365
Outlook
Using Stellar Repair for Outlook to Recover a Corrupted PST
This post was Sponsored by Stellar Repair, you can learn more about their PST Recovery Tool here. Email is the de facto standard for today’s business communications. Businesses rely on email for personal communications, team assignments, announcements, and notifications as well as purchasing and other intracompany communications. This has been particularly true during the recent…
Last Update: May 10, 2024
Apr 7, 2021 -
Microsoft 365
Understanding Microsoft 365 Data, What is and Is Not Your Responsibility
When people talk about the security of data in Microsoft 365, invariably phrase you’ll hear – and I don’t know who coined it – “the cloud is just someone else’s computer”. When someone says it to me, I literally have to stop myself from saying “…but actually” before we both explode into memes. Microsoft 365…
Last Update: May 10, 2024
Apr 1, 2021
PODCASTS
View all Podcasts-
podcast
Top 20 Features in the New Microsoft Teams and Outlook
In this episode of UnplugIT, hosts Darrell Webster and Stephen Rose delve into the latest updates and features in the new Microsoft Teams and Outlook clients. The discussion begins with an overview of Teams’ global rollout and the various enhancements aimed at aligning it more closely with Outlook, such as drag-and-drop calendar support and new…
Listen now LISTEN & SUBSCRIBE ON: -
podcast
Microsoft Announces Big Changes for On-Premises Exchange Server
This Week in IT, I cover everything you need to know about Microsoft’s new edition of Exchange Server, which is due to launch in 2025. Exchange Server will follow a similar path to on-premises SharePoint and the new edition will also bring with it some new features. Thank you to Semperis for sponsoring this episode…
Listen now LISTEN & SUBSCRIBE ON:
OUR SPONSORS
-
Cayosoft
Learn more about CayosoftCayosoft delivers the only unified solution enabling organizations to securely manage, continuously monitor for threats or suspect changes, and instantly recover their Microsoft platforms.
-
ManageEngine
Learn more about ManageEngineMonitor, manage, and secure your IT infrastructure with enterprise-grade solutions built from the ground up.
-
Semperis
Learn more about SemperisReduce time to recover AD after a cyberattack by up to 90%. With Semperis Active Directory Forest Recovery (ADFR), you’ll be back in business in minutes or hours rather than days or weeks.
-
SkyKick
Learn more about SkyKickEngage with 100% of your customers with personalized data