How External Access for Microsoft Teams Works

Teams Gets Guests
Long anticipated and much promised, Microsoft launched external access for Teams on September 11 (here’s a link to Brad’s news story). Well, they posted a blog describing the principles used for the design (motherhood and apple pie – teamwork, security and compliance, and manageability). Releasing code that worked and satisfied those principles took a little longer and tenants reported some frustration that Teams and web clients had not received the updated code. It takes time to distribute new bits across Office 365 and tenants gradually received updates with the necessary code (version 1.0.00.25151 of the desktop client works).
External access for Teams is now available to all Office 365 commercial and education customers. The new feature allows Teams to compete with the likes of Slack and Hipchat. Office 365 Groups has supported external access since August 2016. However, the groups developers chose to build their external access around the existing model used for SharePoint. On the one hand, this was a good decision because it delivered external access faster. On the downside, external members of groups can access the files in the SharePoint team sites belonging to groups, but they cannot browse conversations or the group calendar.
Given that Teams brings together resources from many Office 365 applications, Microsoft needed to make sure that their selected access mechanism delivered secure, robust, and reliable access to anything in a team. Doing so created some engineering difficulties that took more time to resolve than originally predicted.
But Only for Azure AD Accounts
For now, the external access for Teams is only for users with Azure AD accounts belonging to Office 365 tenants. As Microsoft notes in their announcement:
“Later, we’ll add the ability for anyone with a Microsoft Account (MSA) to be added as a guest in Teams. If the guest doesn’t have an existing MSA, they will be directed to create a free account using their current corporate or consumer email address, such as Outlook.com or Gmail.com.”
Azure AD, Guests, and Invitations
External guests are represented by guest objects in Azure Active Directory and leverage the B2B collaboration infrastructure built for the directory. You can create guest user objects through the Azure portal with the Invite a Guest option (or with PowerShell). In either case, you enter the email address of the external user.
Azure AD supports the creation of guest accounts for email addresses from another Office 365 tenant, an on-premises organization, or a consumer email service like Outlook.com or Gmail. When created, you see and can manage guest users in the Office 365 Admin or the Azure portal. You know guest users in Azure AD because their UserType property is “Guest” and their UserPrincipalName is based on their email address in the form:
Tony.Redmond_OtherDomain.com#EXT#MyDomain.onmicrosoft.com
To list all the guest user accounts for your domain, you can run the Get-AzureADUser cmdlet:
[PS] C:\> Get-AzureADUser -Filter "UserType eq 'Guest'" | Sort DisplayName | Format-Table DisplayName, UserPrincipalName
When Azure AD adds a new guest user object, it calls the Invitation API to create and send an invitation via email to the user’s address to tell them that they have been invited to start using an application in your domain. The Invitation API allows the application generating the invitation to include a link for the user to enter the application, like the access information for an Office 365 Group or Team.
If the guest already has a Microsoft account (belonging to another Office 365 tenant or an MSA account), they can go ahead and use that account. If not, Azure AD goes through a redemption process to make sure that the guest can sign in.
All Azure B2B applications work in the same manner (including Groups and Teams). The difference is the link contained in the invitation – it can point to an individual team, group, or other application and the application referenced must be ready to allow access to that guest user. Making sure that Teams is ready to handle guest user access is the core of the new feature.
Controlling Licenses
The Teams settings in the Office 365 Admin Center control whether external users have access to Teams in the tenant. Go to Settings by user/license type and select Guest in the drop-down. Then move the slider for Turn Microsoft Teams on or off for users of this type to “On” (Figure 1) and save the settings. External access is now available for all teams in the tenant.
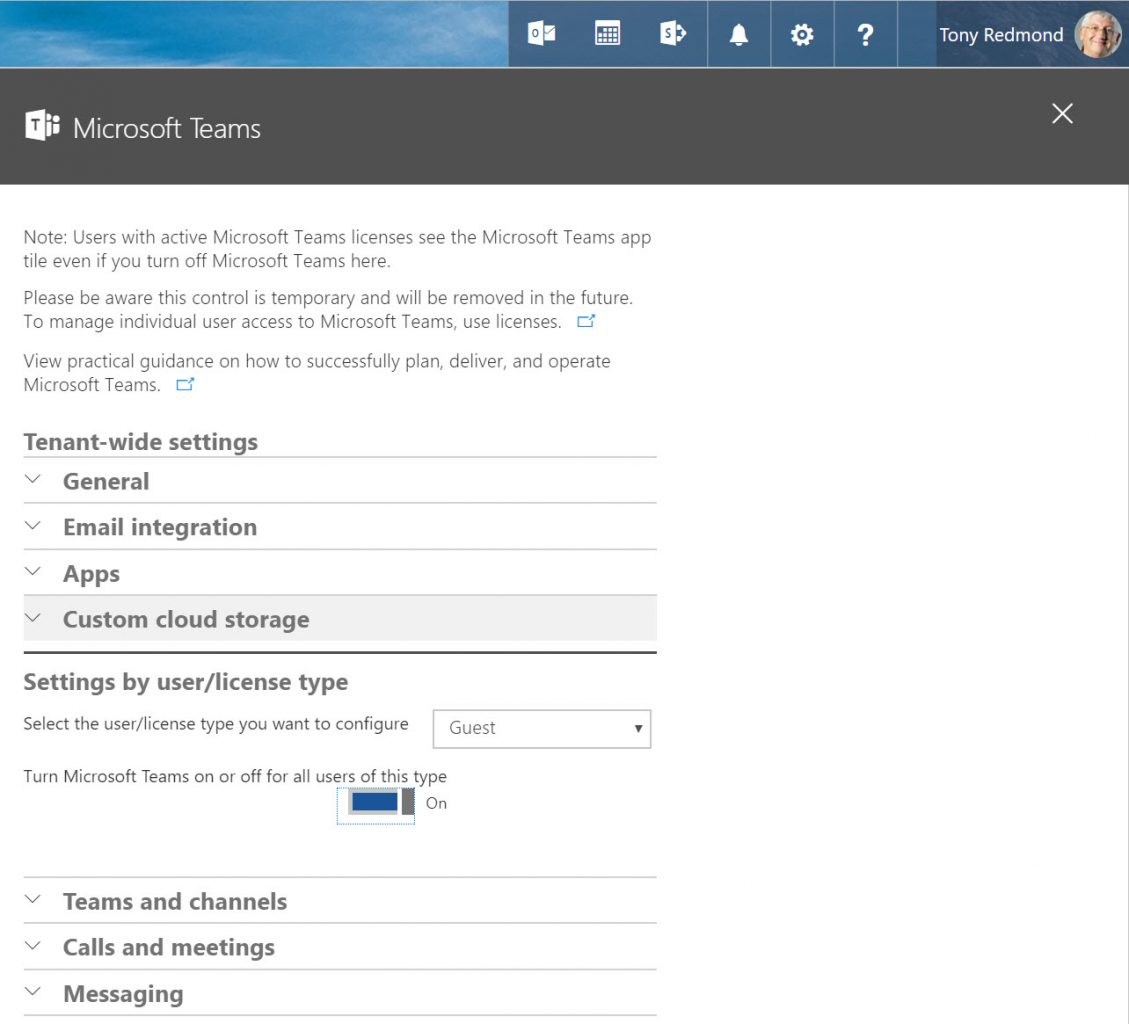
In addition, check the settings for Office 365 Groups in the Office 365 Admin Center to make sure that the slider to Let group members outside the organization access group content is On. This ensures that access to the SharePoint site owned by groups and used by Teams is available.
Adding External Members to Teams
To add a new external team member, a team owner or Office 365 Admin uses the web or desktop client to select the team and then Add members (right-click menu). Input the email address for the new member and click Add Member (Figure 2). You can input the email addresses of people who do not have Azure AD accounts connected to an Office 365 tenant (like Outlook.com) and Teams will add these as external members. However, until Microsoft supports non-Azure AD accounts, they will not be able to access Teams.
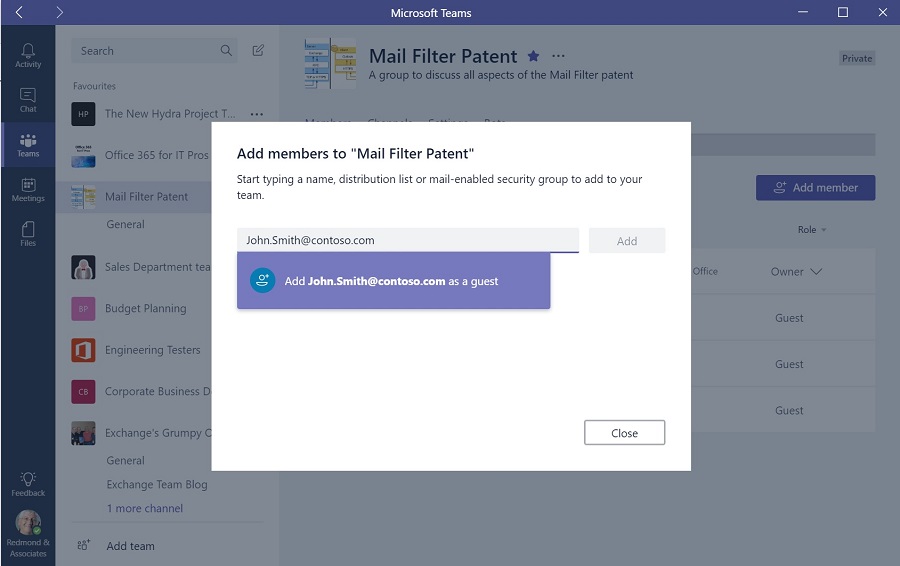
To make everyone in the team aware that someone external is joining, Teams posts a notification in the General channel to tell them that the owner has added a new guest.
An Invitation Arrives
Teams generates and sends the invitation, which holds all the information necessary for the recipient to know about the team they are joining, including a GUID to find the right Office 365 tenant and another GUID for the team. The recipient must redeem the invitation by clicking the Open Microsoft Teams link in the message (Figure 3).

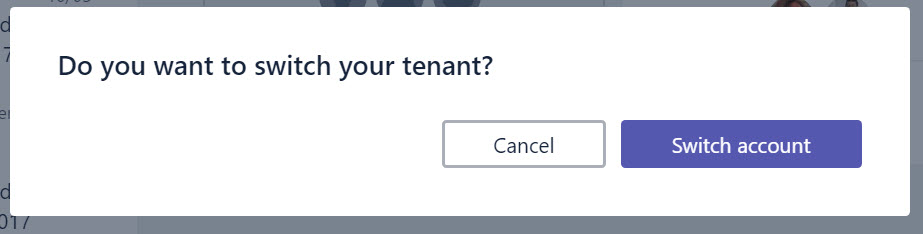
Switching Between Tenants
If the Teams desktop app is available, Teams launches it to access the target team. This means that Teams needs to sign-out from your home tenant and sign-into the target tenant (Figure 4). Switching is quick and painless. That is, if your client software is at the right version and the target tenant allows external access to Teams. If not, you might go into a whirl of unhappiness and will never be able to connect to the remote tenant.
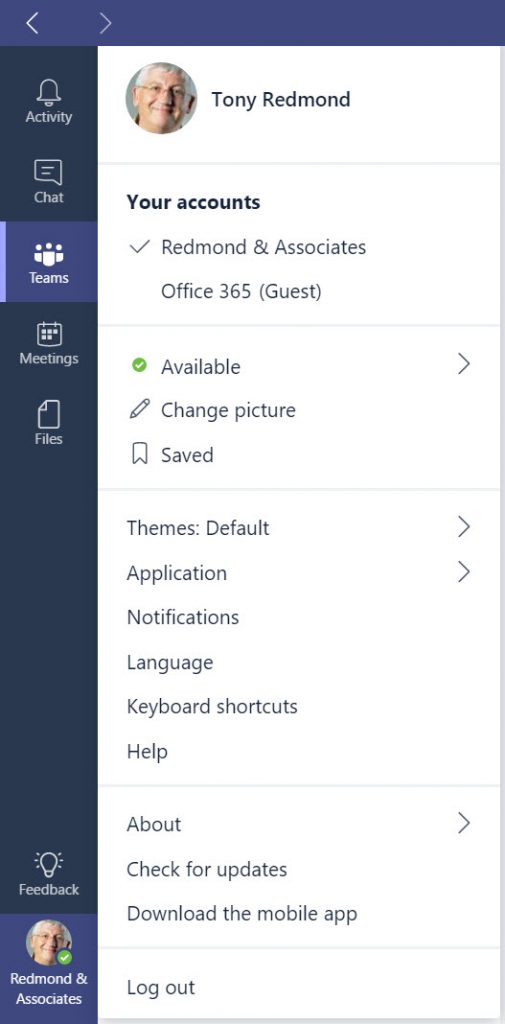
The need to switch to a different context for the client within the target tenant is understandable and is like the approach used by Yammer when a user switches networks. Later, you can return to your home tenant by clicking on your photo in the lower left-hand corner and selecting your home tenant from the list of accounts (Figure 5).
Microsoft has not yet updated the Teams mobile client but have said that messages posted by external members appear in the mobile clients and that an update is on the way to support switching between tenants.
Identifying Guests
Teams gives some visual hints to users that the discussions and other content shared in the team is available to external members. First, a banner with “This team has guests” appears under the team name in the client. Second, external members have a “(Guest)” suffix in member lists (Figure 6). The suffix also shows up when guest users contribute to chats within the team. You can also see the warning that “This team contains users from outside your organization,” just in case the guest suffix is overlooked.
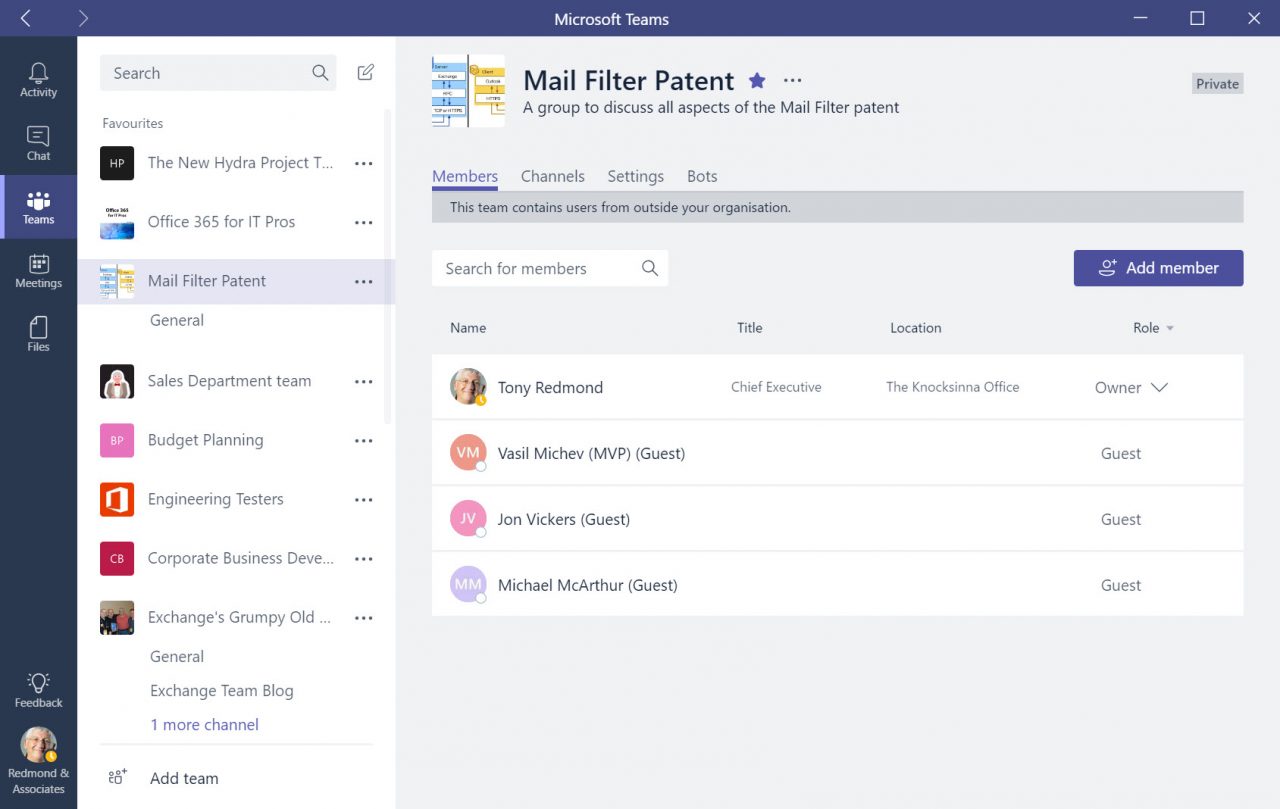
By default, Azure AD guest accounts do not include information like a properly-formatted display name or contact information. It is easy to add this information by editing the account using the Azure Portal or the Office 365 Admin Center. For instance, some tenants like to add the name of the company a guest belongs to in their display name.
You can remove external members from a team in the same way as you remove a tenant user. Select View team from the menu and then Remove for the user in the member list. You cannot remove a user who is a team owner until you demote them to member first. If you want to remove an external user from all teams in a tenant, you can remove their guest user object from Azure AD. Removing an external member from a team does not remove the Azure AD guest user account. If you want to remove a guest account, you can do this from the Azure portal, the Office 365 Admin Center, or by running the Remove-AzureADUser cmdlet, which then removes the guest from all teams and groups that it had joined.
What External Team Members Can Do
Table 1 lists the functionality available to external team members and compares it with the functions available to users belonging to the host tenant. All the functionality you expect is there, like being able to join in private and public chats using IM, video, and audio (and as Håvard Øverås pointed out to me, even chat with Skype for Business users). You can work with the shared OneNote notebook and the files in the SharePoint team site. However, when I tried to access Planner, the sign-in took me to my own tenant and the plans stored there. This is what I expected because Planner does not yet support external access and underlines the point that just because one app supports access, you cannot assume that everything that tenant users can get through via the app enjoy the same access.
| Teams feature | Tenant users | External Guests |
| Create a channel (team owners control this ability through team settings) | Yes | Yes |
| Join in private chats | Yes | Yes |
| Join in public (channel) conversations | Yes | Yes |
| Post, delete, and edit messages | Yes | Yes |
| Upload file to document library | Yes | Yes |
| Share a file (in SharePoint) | Yes | Yes |
| Share a file in a personal or public chat | Yes | Yes |
| Add apps (bots, tabs, or connectors) | Yes | No |
| Invite guest users outside the Office 365 tenant | No | Yes |
| Create a new team | Yes | No |
| Discover and join public teams | Yes | No |
| View organization chart | Yes | No |
| Schedule meetings | Yes | No |
Table 1: Functionality available to tenant and guest users (source: originally Microsoft – with some updates)
Some control over the features available to guests is available to team owners. Right-click a team name and select View team from the menu. Go to the Settings tab and select Guest permissions. You can then select whether guests can create, update, or remove channels. You cannot upgrade a guest to become an owner of a team,
The standard Teams features that external users cannot access are logical and in line with how external access works for Office 365 Groups. No one wants external people to be able to browse your corporate directory, create their own team, or look for other teams to join.
Teams and Groups
Teams uses Office 365 Groups for its membership service and Groups also supports external members. It therefore follows that if you have a group with external members, those members should have access to the team belonging to the group.
What confused me is that if you open the General channel for a team belonging to a group that has external members, you see a series of notifications saying that the team owner removed people from the team (Figure 7). These are the external members in the group and removing them from the team seemed to show that Teams and Groups keep separate membership lists.
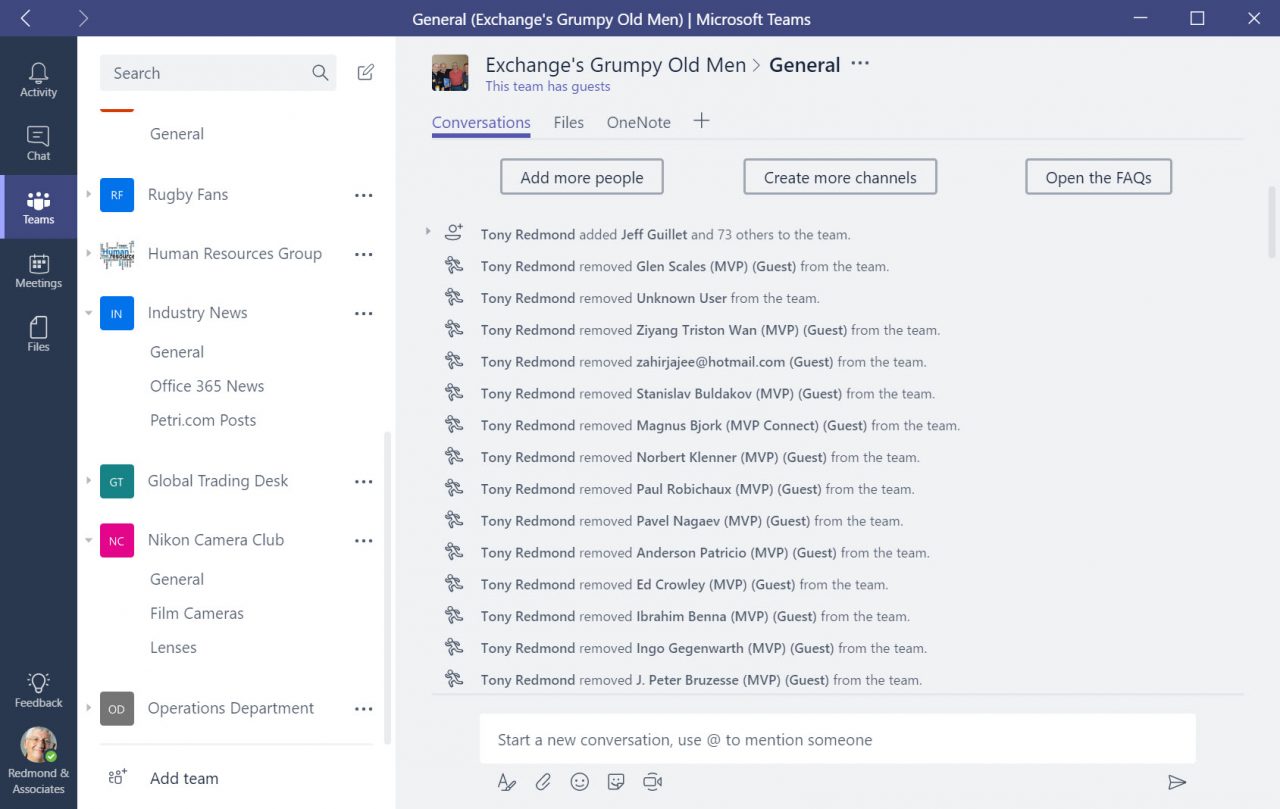
Teams and Groups share common membership and what happened here is that when Microsoft first enabled external access a process ran to remove external users from Teams. Once the tenant enabled external access for Teams, the guest members were supported again and a process runs to restore them to the team. You can add new guest users as you wish and if you add a new external member to the team who was never a member of the group, they show up in the group membership.
A Domain Blocking Policy
In August 2017, Microsoft released an external block policy for Groups, Teams, and Planner. The policy allows Office 365 tenants to define a block or an allow list for domains for external access (but not both). For instance, you can define a block list to stop team owners adding people from competitor domains as external members of teams.
Moving Forward
Adding the ability to add people with Azure AD accounts as external members of Teams is a good step forward. The true power of this capability comes when you can add anyone (policy permitting) with any email address as an external member. But for now, if you need to share Teams between Office 365 tenants, all the necessary tools are in place.
Follow Tony on Twitter @12Knocksinna.
Want to know more about how to manage Office 365? Find what you need to know in “Office 365 for IT Pros”, the most comprehensive eBook covering all aspects of Office 365. Available in PDF and EPUB formats (suitable for iBooks) or for Amazon Kindle



