How can I tell if an SSL certificate has expired or not before I enter the secured site?
Any website operator that wants to secure the site or some of it’s pages with SSL must obtain a valid certificate from a trusted third party CA.
If you try to enter a secure website that uses an expired certificate, like the MCP Secure site on Microsoft’s website at http://www.microsoft.com/traincert/mcp/mcpsecure.asp you will get a secure website warning (This was true on the 26th of January 2003, but 2 days later it was fixed without great success – read more about it on the Untrusted Certificate Source page):
If you click OK your web browser will try to obtain the signed certificate from the web server, but if that certificate is obsolete you’ll get this warning:
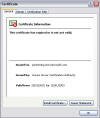
You can choose to view the certificate and if you do you’ll see (on the General tab) the reason for the error message:
If you click on the Details tab you can see that this specific certificate is outdated (although the screenshot is in Hebrew it’s still correct):
If you choose to agree to accept this certificate you will be able to enter the secure site, providing it is indeed a secure and valid site, and not an exploit or a redirected malicious site.
Note: Having respected sites like Microsoft’s use expired certificates or certificates from un-trusted CAs is somewhat irresponsible in my opinion. Any hacker or malicious user with little HTML, X500 and hacking knowledge can easily divert the innocent and un-expecting users to a malicious site (by breaking into the DNS servers that are authoritive for the microsoft.com domain) where he or she can easily create a similar digital certificate. Users will then be tempted to accept the certificate although it is clearly either expired or (what’s even worse) from un-trusted CA (one that the hacker himself can easily set up by using Microsoft-like domain names). People who will log on to the so-called secure site with their MSN Passport accounts will then be giving this information to the hacker, which in turn can use this information to do wrong or even steal other information.
Related articles
You might also want to read the following related articles: