Exchange Online Protection Highlights Unauthenticated Senders
EOP’s Ongoing Fight to Protect Office 365
Although some might complain that the rate of change in a cloud service like Office 365 is too fast, one advantage gained is availability to new protection techniques for email as soon as they are ready. Malware evolves all the time as hackers, spammers, and phishers search for new vulnerabilities. The battle against new attack vectors is ongoing and constant.
Few tenants have the time, energy, or knowledge to fight malware attackers on their own, which is why it is good to have Microsoft’s security team do the heavy lifting for Office 365 as part of Exchange Online Protection (EOP).
Highlighting Dubious Email
Recently, Microsoft has added support for dynamic delivery and safety tips in EOP. The latest innovation is highlighting messages received from unidentified sources to give recipients a visual warning to take care. It is part of the array of technologies deployed within EOP like SPF, DKIM, DMARC, and anti-spoofing to verify the identity of message senders.
Ideally, any email you receive should come from a domain that publishes its credentials for all to check, like a DKIM signature. Unfortunately, some organizations continue to ignore the need to publish credentials. This might be by oversight, but often a malicious intent exists because an attacker wants to exploit technical or social weaknesses in target domains through malware.
The latest advance means that when Exchange Online Protection cannot verify the sender of a message using the array of techniques deployed for checking, it considers the message to come from an unidentifiable source. OWA notifies the user by displaying a question mark instead of the sender’s photo (if one is available) or their initials. Because Office 365 and Outlook.com share the same email infrastructure, the same protection is available to both business and consumer users.
Some Messages Smell Bad to EOP
If you see a big question mark where a user photo should be, it is a big sign that something smelly exists in the message. For some reason, EOP cannot satisfy itself that the message originates from a domain that it can check. These messages appear valid enough to avoid EOP redirecting them to the junk mail folder, but they are suspicious enough to call for some added care when opening.
The standard is that if a message does not pass both the SPF and DKIM tests, it is marked as suspicious and you see a question mark for the user photo (Figure 1).
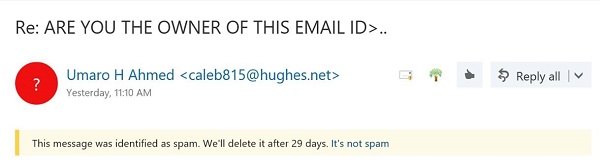
You can check these results by examining the message header using the Message Header Analysis add-in. Click Other to view the authentication results. In Figure 2, you can see that the SPF result is “none” and the DKIM result is also “none,” meaning that this is a problematic message.
Admin Snafus Can Make EOP Suspicious
Although a highlighted message might an attempt to spoof the recipient, it is entirely possible that an administrative slip-up on the part of a sending domain is why EOP regards their messages with suspicion. The global nature of email and the mass of interconnected systems that exchange messages with each other means that standards are hard to apply, especially when legacy email systems persist long past their best-by date. The ecosystem is not perfect and anti-malware checks are sometimes imperfect too, which is why some messages turn up in user inboxes when they should really be marked as junk mail.
Highlighting doubtful messages with question marks should prompt recipients to be more careful about how they handle this email. Hopefully, people will look at the sender information and ask whether they expect email from this source before they open a flagged message. At least, that is the theory.
EOP stamps dubious messages to force clients to highlight them even when rules process the messages and move them out of the Inbox to other folders. The only way for a domain to stop EOP highlighting its messages when they arrive into Office 365 is to do a better job of authentication with SPF or DKIM. Once a domain can prove its identity to the satisfaction of EOP, it stops stamping inbound messages from that domain as suspicious
OWA is the first client to support the highlighting of suspicious messages. Other Outlook clients might support this feature in due course, but Microsoft is not saying when.
Gmail Does the Same
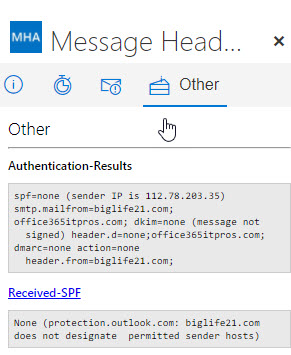
Gmail takes much the same approach to flag suspicious messages (Figure 3). In fact, Gmail was first to this party as they implemented the highlighting of email that cannot be authenticated in February 2016. Microsoft decided to follow the same path to minimize the disruption to people who switch between Office 365, Outlook.com, and Gmail (like me!)
However, Microsoft says that their processing takes factors into account that Gmail. For example, EOP excludes messages sent between Office 365 tenants, which do not have SPF and DKIM results. In addition, some well-known mailing lists do not comply with DKIM, SPF, or DMARC, but as Microsoft is aware of these lists, they exclude them too. In all cases, passing the test with either SPF or DMARC is enough to make the question mark go away.
A Question of Granularity
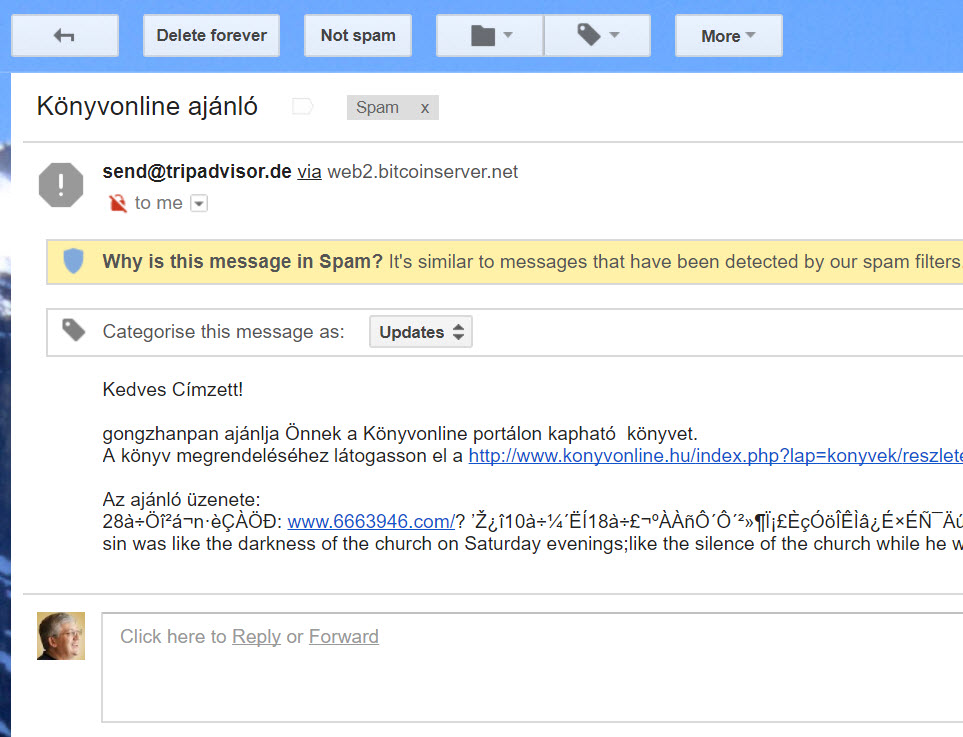
Some might ask the question why not simply move suspicious messages into Junk Email. After all, it is probably safer to put bad messages somewhere safe. The problem is granularity. Some email is obvious spam, like an offer from someone to give you millions of dollars if only you will send them a little cash to grease the wheels of commerce. Who would not want to accept the kind offer extended in a message such as the one shown in Figure 4?
On the other hand, some messages are only mildly problematic. These are the messages highlighted by EOP because, in a way, only the careful perusal by a human will answer the question whether the content is malicious.
The Fight Continues
Malware will not disappear anytime soon. Spam and other malicious content is still a viable attack vector and continues to generate cash for spammers and other miscreants. For the spammers, continuing their activities is a simple economic equation. If they turn a profit, they continue. If not, they go and find another way to extract cash from their unwary. Microsoft has some of the best security researchers in the business helping to protect Office 365. I am glad that they are there and continue to evolve new techniques to protect my email.
Follow Tony on Twitter @12Knocksinna.
Want to know more about how to manage Office 365? Find what you need to know in “Office 365 for IT Pros”, the most comprehensive eBook covering all aspects of Office 365. Available in PDF and EPUB formats (suitable for iBooks) or for Amazon Kindle.