Enabling HTTPS on Windows Server 2008/2012 Certificate Authority for Web Enrollment
When you install a Certificate Authority (or CA) on a Windows Server 2008/R2/2012, it is usually for the purpose of issuing digital certificates. These are then used by users, computers, devices, and so on to authenticate themselves, to prove their authenticity, and for other types of communication that requires Public Key Infrastructure (PKI) encryption. In today’s article I’ll walk you through how to enable HTTPS on Certificate Authority for Web Enrollment, how to create the certificate template, and more.
Issuing Digital Certificates with Certificate Authority Web Enrollment
I will not go into more detail as to why and how you want to install this CA just now (although that’s something that I will probably cover in a later article). However, assuming you know a bit about Windows-based CAs, there are basically four common methods of issuing these certificates:
- Auto-enrollment, in which many types of certificates can be distributed without the client even being aware that enrollment is taking place. These can include most types of certificates issued to computers and services, as well as many certificates issued to users.
- Another method is enrollment through the Automatically Enroll and Retrieve Certificates from the certmgr.msc console.
- CNG Application Programming Interface (API) in Windows Server 2008/R2/2012, and CryptoAPI in previous versions of Windows Server.
- Then there’s Web Enrollment (the default URL is http://CA-Name/certsrv), which I’ll specifically talk about in this post. This is where CA-Name is the name of the issuing Certificate Authority. The Certification Authority (CA) Web Enrollment role service provides a set of web pages that allow interaction with the Certification Authority role service.
Note: You can install the CA Web Enrollment on a server that is not a CA to separate web traffic from the CA. Installing CA Web Enrollment configures the computer as an enrollment registration authority. You must select a CA to be used with the CA Web Enrollment pages. The CA that CA Web Enrollment uses is called the Target CA in the user interface.
You can perform the following tasks from the CA Web Enrollment pages:
- Request a basic certificate
- Request a certificate with advanced options
- Check a pending certificate request
- Retrieve the certification authority’s certificate to place in your trusted root store or install the entire certificate chain in your certificate store
- Retrieve the current base and delta CRLs
- Submit a certificate request by using a PKCS #10 file or a PKCS #7 file
Request a Certificate
So, you’ve installed your CA, added the Web Enrollment role service, and now you would like to request a certificate or perform one of the tasks described above.
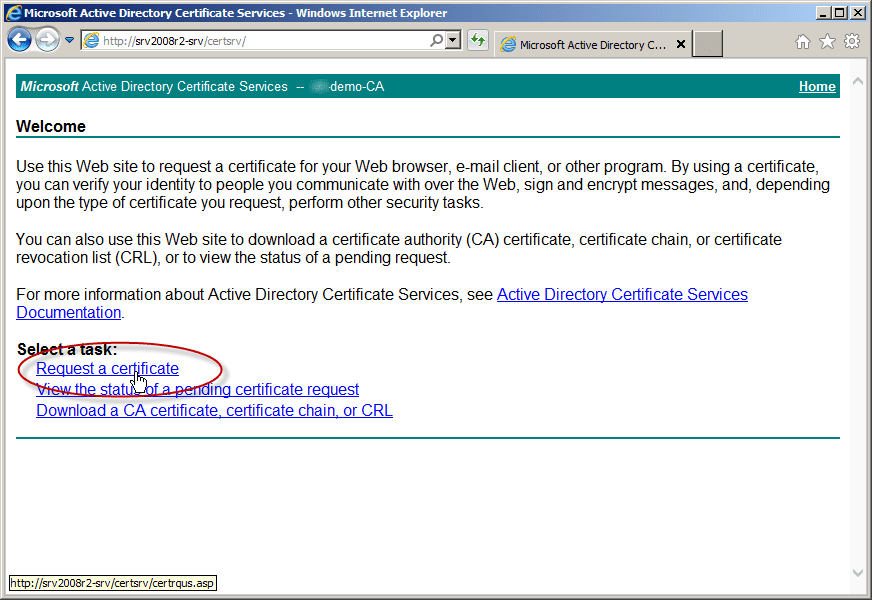
- First, open a web browser window and navigate to http://CA-Name/certsrv and click on Request Certificate.
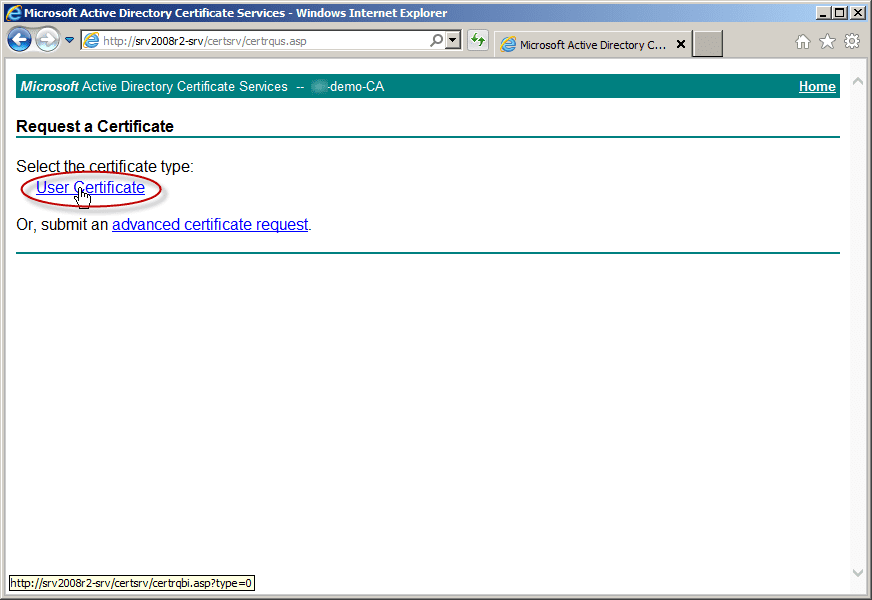
- Next, click on the type of certificate you want to issue (in this case, it’s a user certificate).
The next thing you will see is an error reading, “In order to complete the certificate enrollment, the Web site for the CA must be configured to use HTTPS authentication.”
The reason for this error is that the CA Web Enrollment role service pages require that you secure them with secure sockets layer (SSL) / transport layer security (TLS). To resolve this issue, you must install an appropriate certificate on the web server hosting the CA Web Enrollment pages. In addition, you must configure the Site Bindings for the website to add the HTTPS port 443 binding.
Create the Certificate Template to Issue
Before we begin, we need to make sure that the server hosting the Web Enrollment service role and IIS can enroll and receive a digital certificate that is intended for the purpose of of “Server Authentication.” This means that they must contain the Server Authentication object identifier (OID): 1.3.6.1.5.5.7.3.1
Read my article, “Creating a Digital Certificate Template for the Purpose of Server Authentication in Windows Server 2008/R2/2012” for more information about this.
Obtain a Certificate for IIS Using the Certificate Template
- Next, on the IIS server hosting the CA Web Enrollment pages, open an MMC console by typing mmc and then pressing Enter.
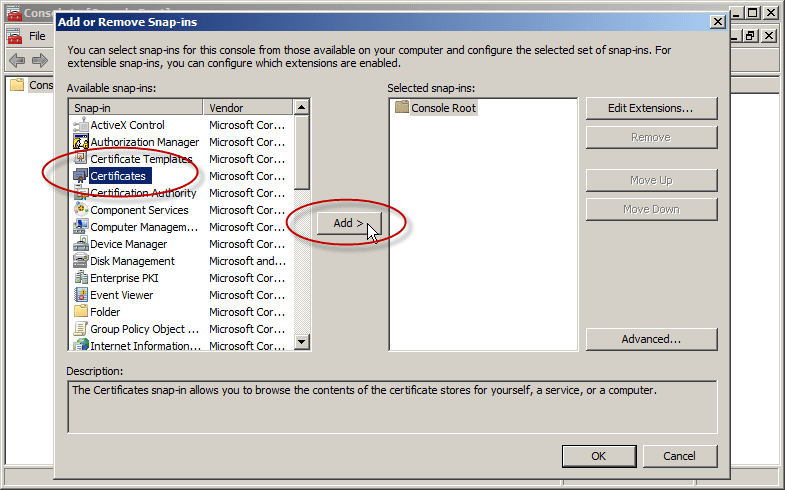
- In the new MMC console (Console1), click File, then click Add/Remove Snap-in.
- From the list of available snap-ins, select Certificates and then click Add.
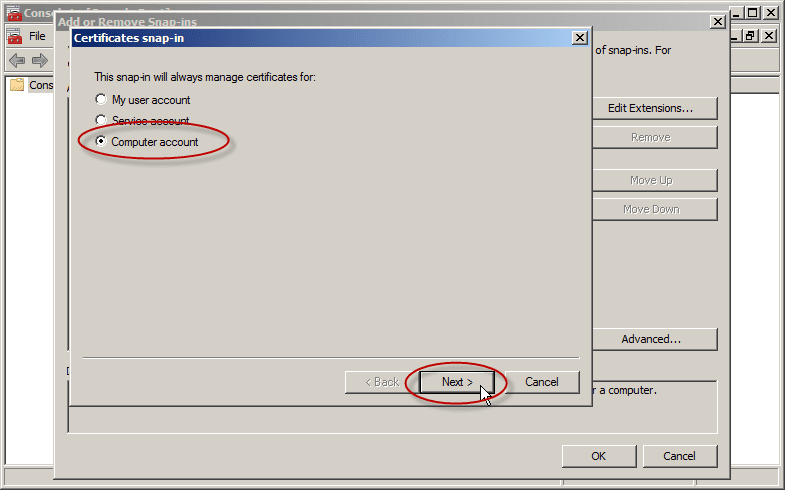
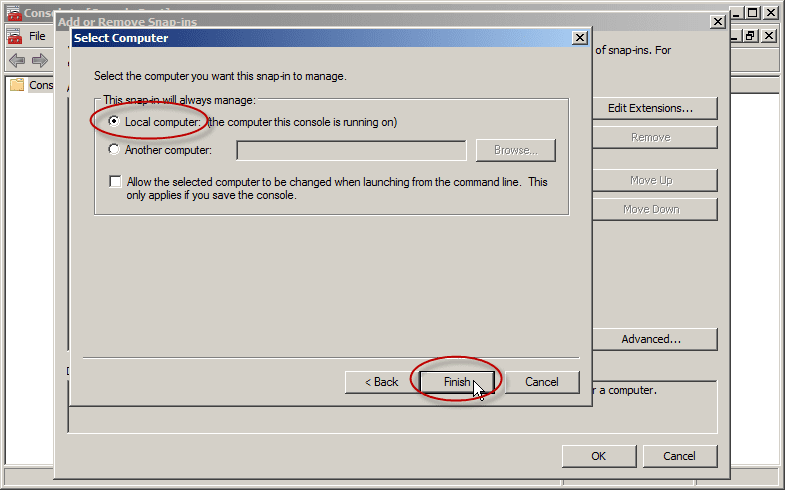
- Select the Computer account and then click Next.
- By default, the Local computer is selected within Select Computer. Click Finish and then click OK.
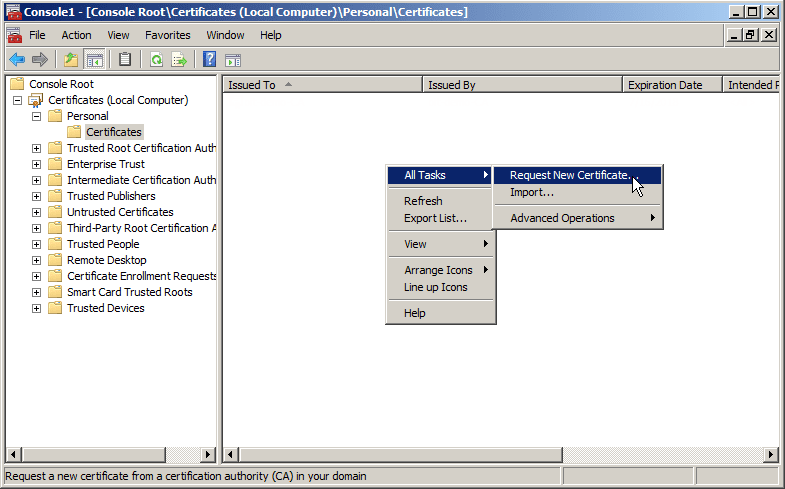
- Expand Certificates (Local Computer) and then right-click Personal. Click All Tasks, and then click Request New Certificate.
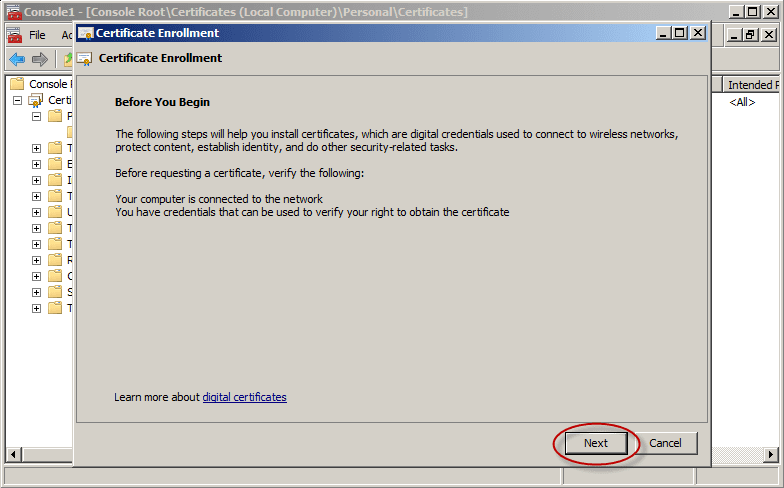
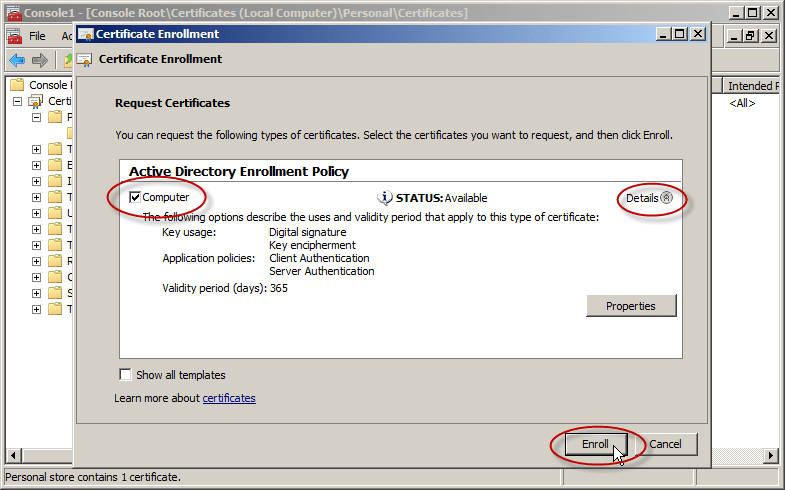
- Click Next in the Certificate Enrollment wizard.
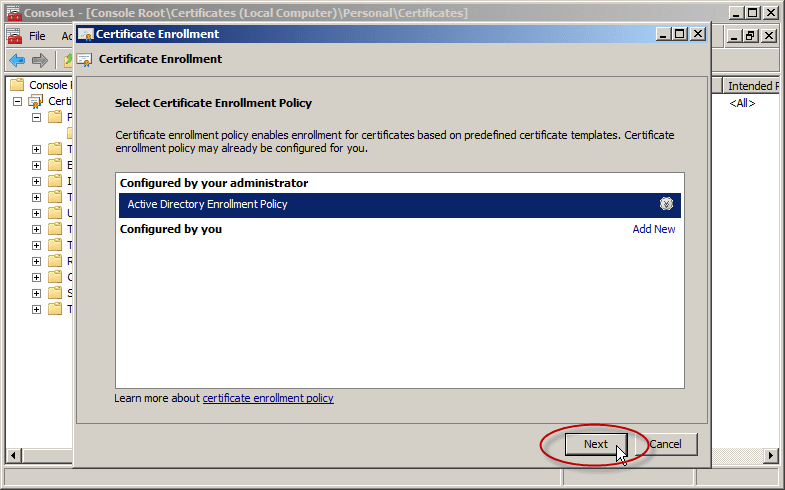
- On the Select Certificate Enrollment Policy page, ensure that Active Directory Enrollment Policy is selected and then click Next.
- On Certificate Enrollment, select the certificate template that is available.
You must make sure that the certificate template you are about to request contains the Server Authentication object identifier (OID): 1.3.6.1.5.5.7.3.1. Read my article, “Creating a Digital Certificate Template for the purpose of Server Authentication in Windows Server 2008/R2/2012,” for more information about this.
- The Computer template does. You can verify this by clicking on the Details arrow. Look at the Application Policies section and select it.
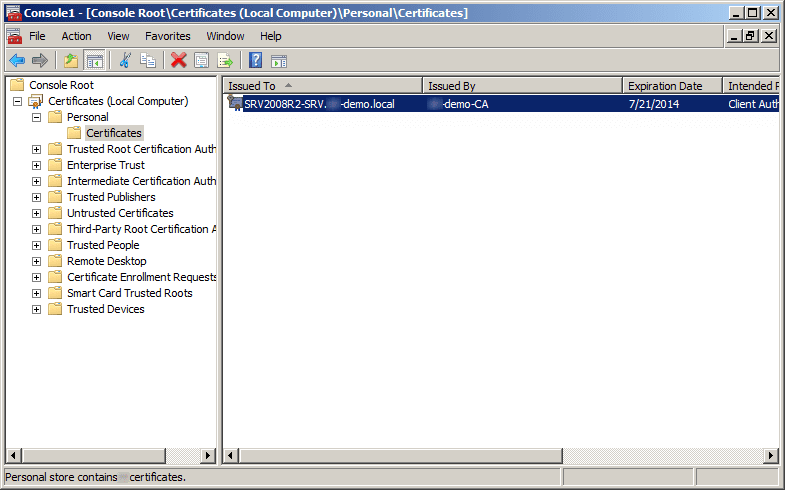
- Click Enroll. Click Finish.
When the process is finished, you will have a brand new digital certificate.
Configure HTTPS on the Default Website
Next, we need to enable IIS to use this certificate and listen (bind) to the right port (TCP 443) for HTTPS connectivity.
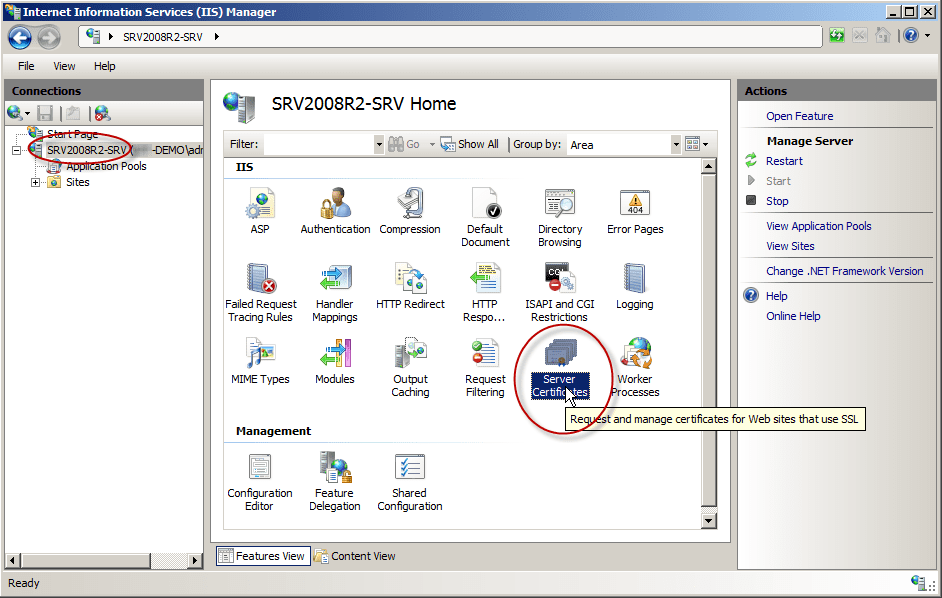
- On the IIS server hosting the CA Web Enrollment pages, open the Internet Information Services (IIS) Manager.
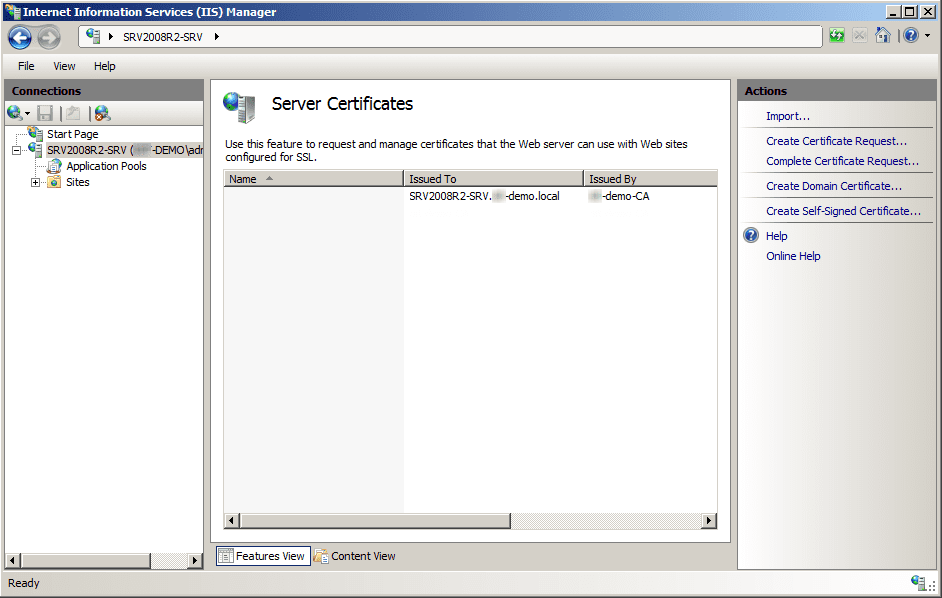
- Click on the server name. In the right-pane, click on Server Certificates.
- Note that our certificate is listed. You can inspect it of you want to.
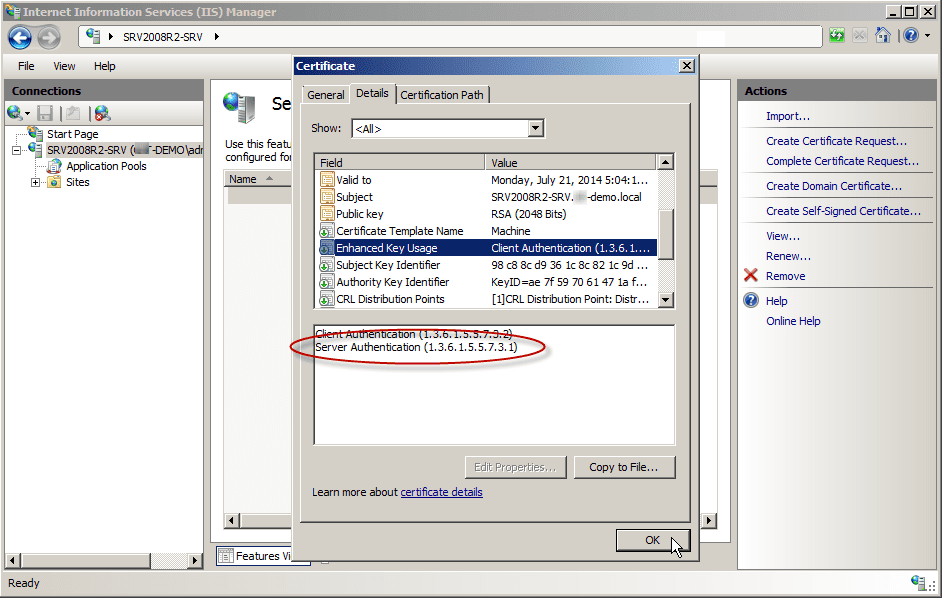
- The certificate’s purpose should be to ensure the identity of a remote computer. To further verify, you can click the Details tab of the certificate.
- Select Enhanced Key Usage and ensure that it reads Server Authentication (1.3.6.1.5.5.7.3.1). Click OK.
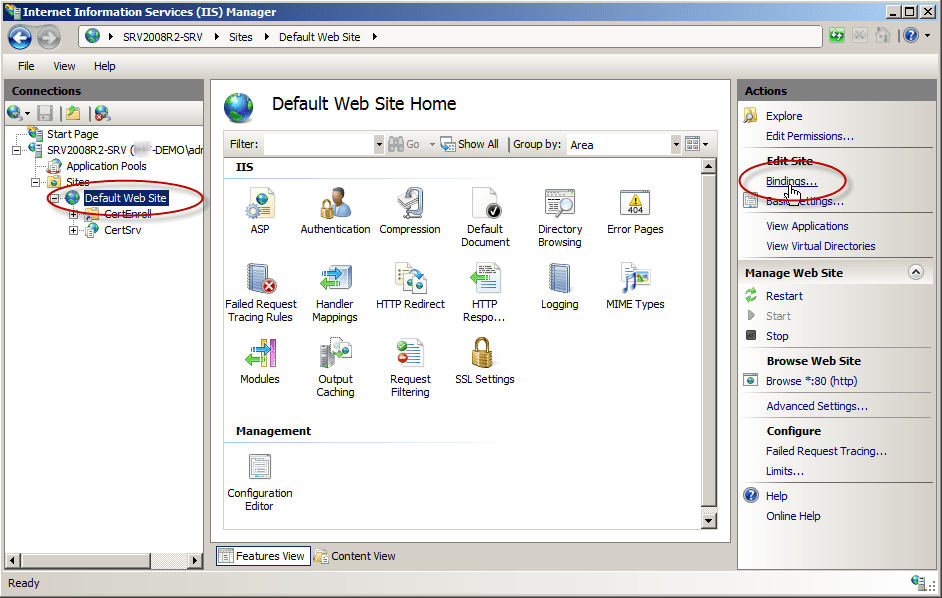
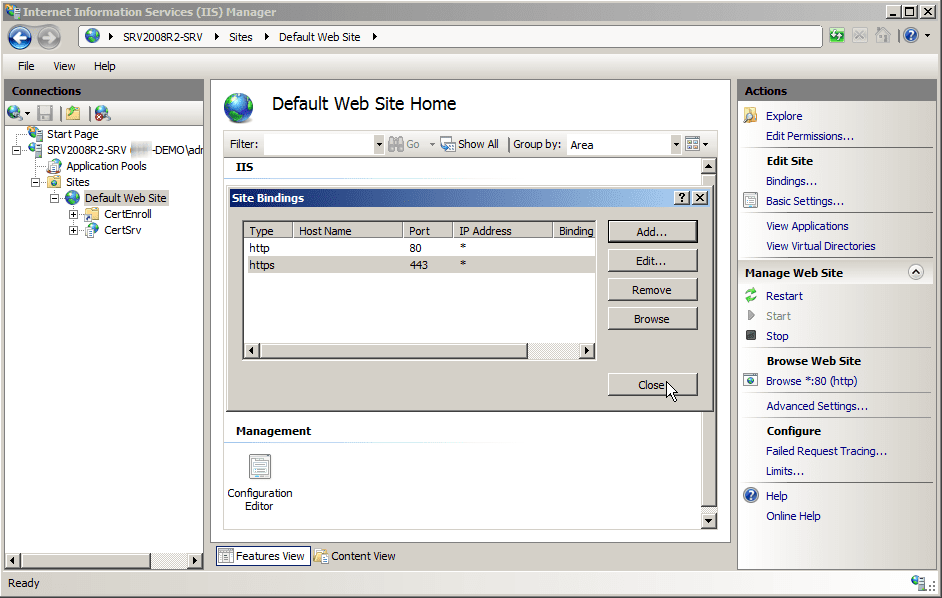
- Expand the server and Sites nodes until you can see Default Web Site. Click Default Web Site.
- On the Actions pane, click Bindings.
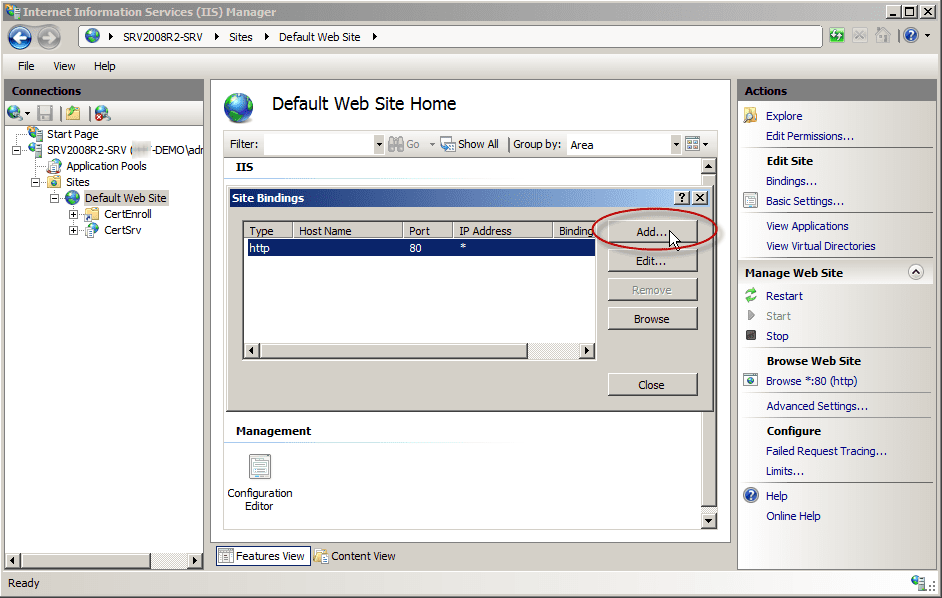
- In Site Bindings, click Add.
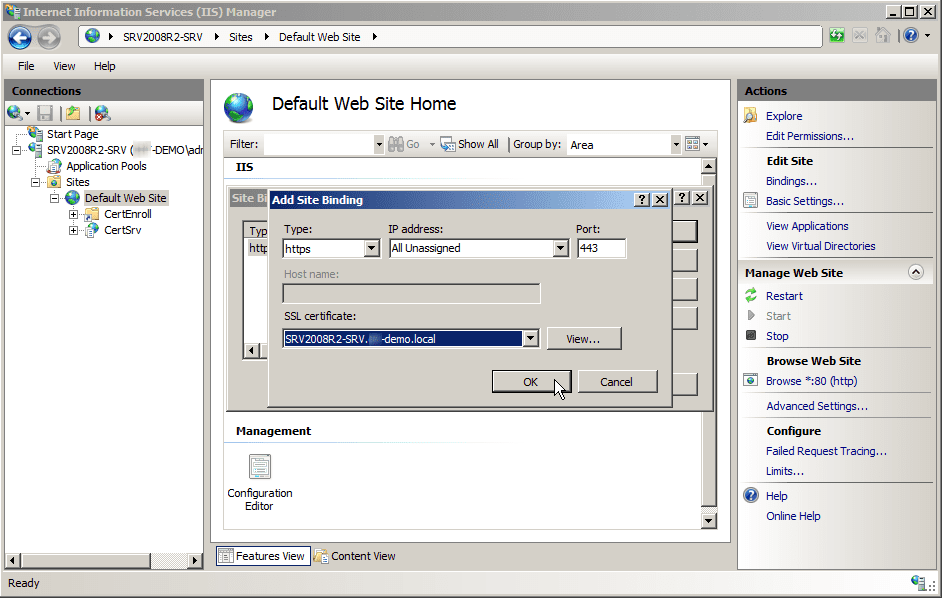
- In Add Site Binding, set Type to HTTPS.
- Set SSL certificate to the certificate that you issued to the server. If you have more than one certificate, you can confirm you have the correct certificate by clicking View.
- On Add Site Binding, click OK.
- On Site Bindings, click Close.
Connect to the HTTPS Location for Certificate Web Enrollment
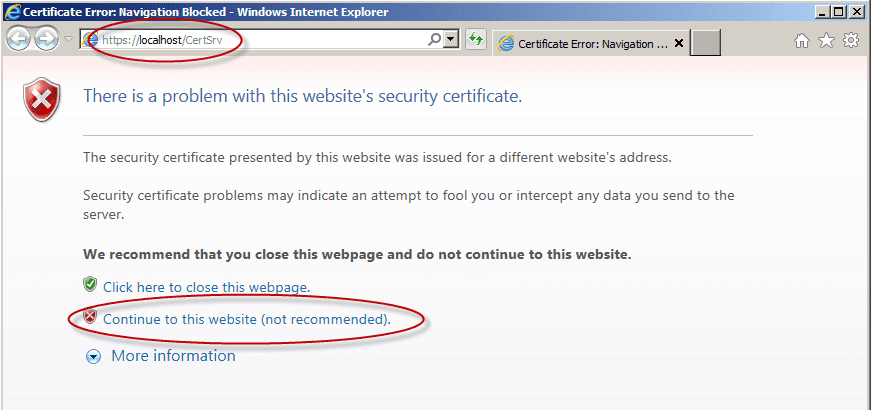
Instead of using the former http://CA-Name/certsrv you must connect to https://CA-Name/certsrv to request a certificate. Now the error is gone.
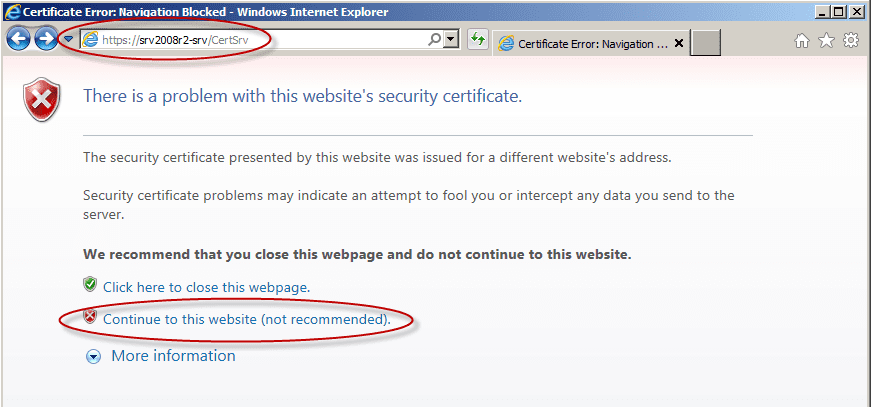
Note: If you attempt to browse to https://CA-Name/certsrv instead of using the server’s name, you may get an error. This is because the server is presenting the browser a digital certificate that claims it is for CA-Name, when in fact you are accessing Localhost.
You can click on “Continue to this website” or correct your URL.
This may also happen if you attempt to use just the host name part of the server’s FQDN. Again, this is because it is not the name to which the certificate was issued.
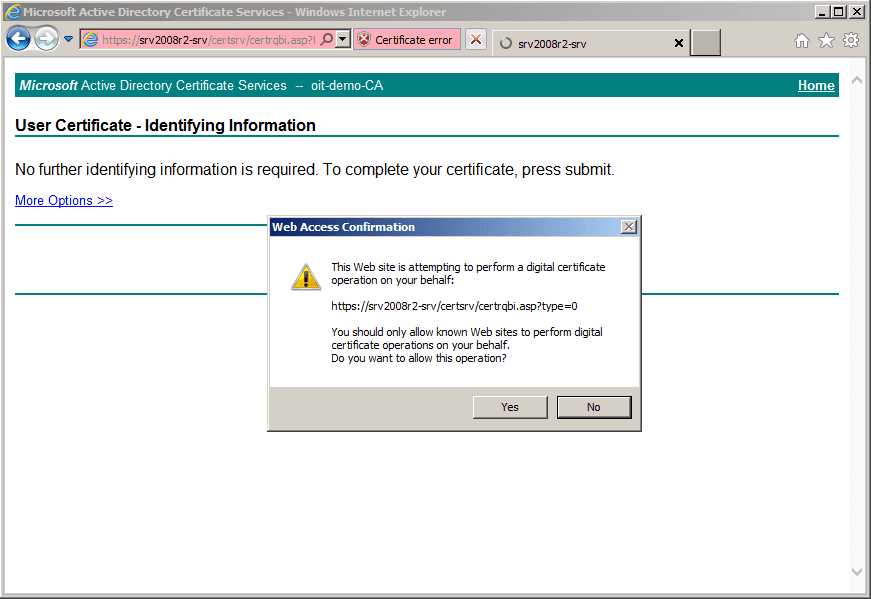
Note: You may be required to enter your credentials.
Did you try to use the servers FQDN and got an error? Read my article, “Solving the ‘This Web Browser Does Not Support the Generation of Certificate Requests’ Error,” for a solution.