Create an Azure Network Security Group using ARM PowerShell
In today’s Ask the Admin, I’ll show you how to create a Network Security Group in Azure using PowerShell.
A year ago I wrote a primer on creating Network Security Groups (NSGs) using PowerShell, which you can read on Petri here. NSGs differ from endpoint-based ACLs in that they can be applied to more than one VM by associating them with NICs or subnets. They also survive the lifecycle of VMs and are typically used to fence off Azure subnets from one another without needing to specify endpoint-based network ACLs for each VM in the subnet.
Microsoft’s new portal for Azure has been made generally available since I wrote the original article, and along with it a new deployment model called Azure Resource Manager (ARM). For a better understanding of ARM, see “What are Microsoft Azure Resource Groups?” on the Petri IT Knowledgebase.
And starting in Azure PowerShell 1.0, ARM has its own distinct cmdlets, which I’ll use in this demo to create a NSG. If you haven’t yet installed Azure PowerShell 1.0 or higher, read “Install Azure PowerShell 1.0 Preview” on Petri.
Before running the code below, you’ll need to have a Resource Group, virtual network (VNET) and subnet. If you don’t already have these resources deployed in your Azure subscription, see “Provision a domain using a Microsoft Azure Resource Manager template” on Petri, where I show you how to deploy a VM running Active Directory, including a Resource Group, VNET and subnet.
Create a Network Security Group
Let’s get started. Open Windows PowerShell ISE, and log in to your Microsoft account using the Login-AzureRmAccount cmdlet. Then run the rest of the code shown below to select an Azure subscription, Resource Group (RG), and to define a variable with a name for the new NSG.
Login-AzureRmAccount # Select a subscription $subscriptionId = (Get-AzureRmSubscription | Out-GridView -Title 'Select Azure Subscription:' -PassThru).SubscriptionId Select-AzureRmSubscription -SubscriptionId $subscriptionId # Select a Resource Group $rgName = (Get-AzureRmResourceGroup | Out-GridView -Title 'Select Azure Resource Group:' -PassThru).ResourceGroupName # Set the NSG name and Azure region $nsgName = 'NSG1' $location = 'North Europe'
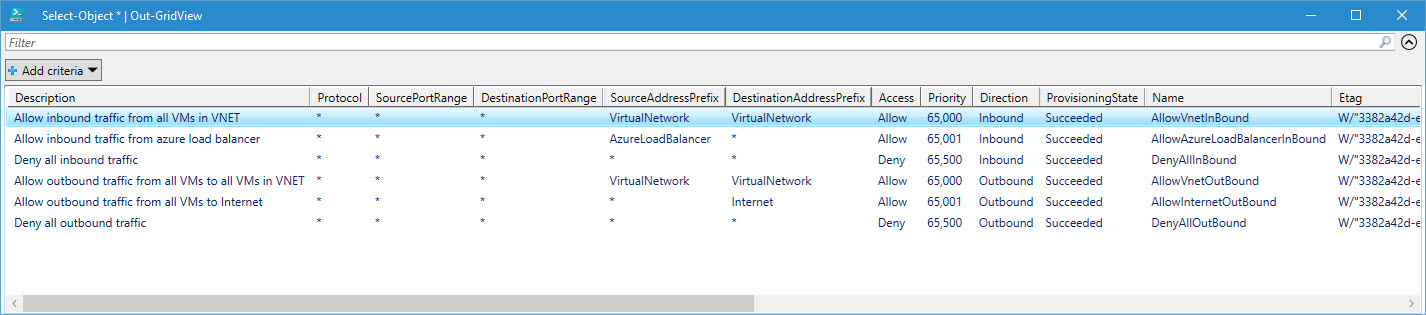
By default, new NSG groups come with a set of default rules to allow inbound and outbound traffic from other VMs and load balancers in the same VNET. Any additional rules must be added manually.
In this example, I’ll add a rule, using the New-AzureRmNetworkSecurityRuleConfig cmdlet, to allow inbound RDP traffic on port 3389. Once the rule is configured, then I’ll create the new NSG using the New-AzureRmNetworkSecurityGroup cmdlet.
# Create the default-allow-rdp rule $rules = New-AzureRmNetworkSecurityRuleConfig -Name 'default-allow-rdp' -Direction Inbound -Priority 1000 -Access Allow -SourceAddressPrefix '*' -SourcePortRange '*' -DestinationAddressPrefix '*' -DestinationPortRange 3389 -Protocol Tcp $nsg = New-AzureRmNetworkSecurityGroup -Name $nsgName -ResourceGroupName $rgName -Location $location -SecurityRules $rules
To view the NSG rule configuration, you can use the Get-AzureRmNetworkSecurityGroup cmdlet as shown here to display the default and custom security rules:
# Display default and security rules for NSG (Get-AzureRmNetworkSecurityGroup -Name $nsgName -ResourceGroupName $rgName).SecurityRules | Select-Object * | outgrid-view (Get-AzureRmNetworkSecurityGroup -Name $nsgName -ResourceGroupName $rgName).DefaultSecurityRules | Select-Object * | outgrid-view
Finally, we need to associate the NSG with a subnet. The Get-AzureRmVirtualNetwork cmdlet is used to retrieve network information so that you can choose which subnet to associate with the NSG. It’s worth noting that the -NetworkSecurityGroup parameter of the Set-AzureRmVirtualNetworkSubnetConfig cmdlet must be a PowerShell object, and not a string.
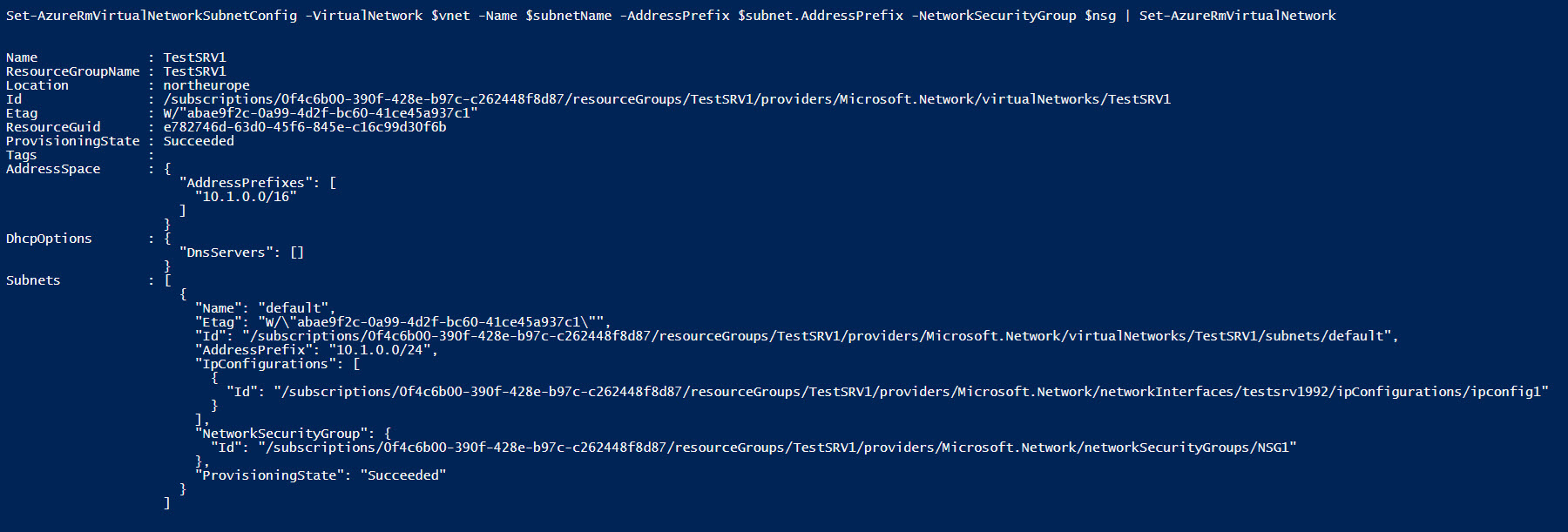
# Select VNET $vnetName = (Get-AzureRmVirtualNetwork -ResourceGroupName $rgName).Name | Out-GridView -Title 'Select an Azure VNET:' -PassThru $vnet = Get-AzureRmVirtualNetwork -ResourceGroupName $rgName -Name $vnetName # Select Subnet $subnetName = $vnet.Subnets.Name | Out-GridView -Title 'Select an Azure Subnet:' -PassThru $subnet = $vnet.Subnets | Where-Object Name -eq $subnetName # Associate NSG to subnet Set-AzureRmVirtualNetworkSubnetConfig -VirtualNetwork $vnet -Name $subnetName -AddressPrefix $subnet.AddressPrefix -NetworkSecurityGroup $nsg | Set-AzureRmVirtualNetwork
In this article, I showed you how to create a new Network Security Group and add a custom security rule using ARM PowerShell cmdlets.




