Active Directory Security: Understanding the AdminSDHolder Object
The AdminSDHolder object manages the access control lists of members of built-in privileged Active Directory groups. In this Ask the Admin, I’ll explain how this mechanism works and how you can change the way that it works.
A couple of months back on Petri, I looked at a new feature in Windows Server 2016: Short-Lived Active Directory Group Membership. In that article, I noted that adding user objects to special AD groups, like Account Operators, might cause the adminCount attribute for the account to be changed to 1 if the account is in the group long enough for the AdminSDHolder mechanism to make the account a protected object. If the adminCount attribute is changed and the account is removed from the group, the adminCount attribute remains set to 1.
The Security Descriptor Propagation (SDPROP) process runs every hour on the domain controller holding the PDC emulator FSMO role. It is this process that sets the adminCount attribute to 1. The main function of SDPROP is to protect highly-privileged Active Directory accounts, ensuring that they can’t be deleted or have rights modified, accidentally or intentionally, by users or processes with less privilege.
SDPROP scans the domain for protected accounts, disables rights inheritance, and applies an access control list (ACL) on the object that mirrors the ACL of the AdminSDHolder container. But if SDPROP determines that an object’s rights inheritance is already disabled and that the ACLs match those of the AdminSDHolder container, then adminCount is not set to 1. So, the adminCount attribute cannot be used as an indicator to determine whether an object is protected. And to further muddy the waters, if a user is removed from a privileged group, the adminCount attribute remains set to 1 and inheritance disabled.
For more information on privileged AD groups, see Managing Privileged Access to Active Directory on Petri.
Controlling SDPROP
SDPROP can’t be disabled but you can change the frequency at which it runs and exclude one or more privileged groups from protection. Changing the frequency is easy. Just create a REG DWORD registry value called AdminSDProtectFrequency on the domain controller that holds the PDC Emulator FSMO role. The value should be added to the following key:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\NTDS\Parameters\
The value of AdminSDProtectFrequency should be between 60 and 7200 seconds (2 hours). Bear in mind that if you have a large directory, setting the frequency to less than 1 hour can put additional load on the domain controller’s processor.
There’s nothing to stop you modifying the permissions and inheritance flag on the adminSDHolder container in AD, although this is not recommended. To modify the container’s ACL, open ADSI Edit from the Tools menu in Server Manager. Connect to the Default naming context and you’ll find the adminSDHolder container under System. For example, if your domain is ad.contoso.com, the path is as follows:
CN=adminSDHolder,CN=System,DC=ad,DC=contoso,DC=com
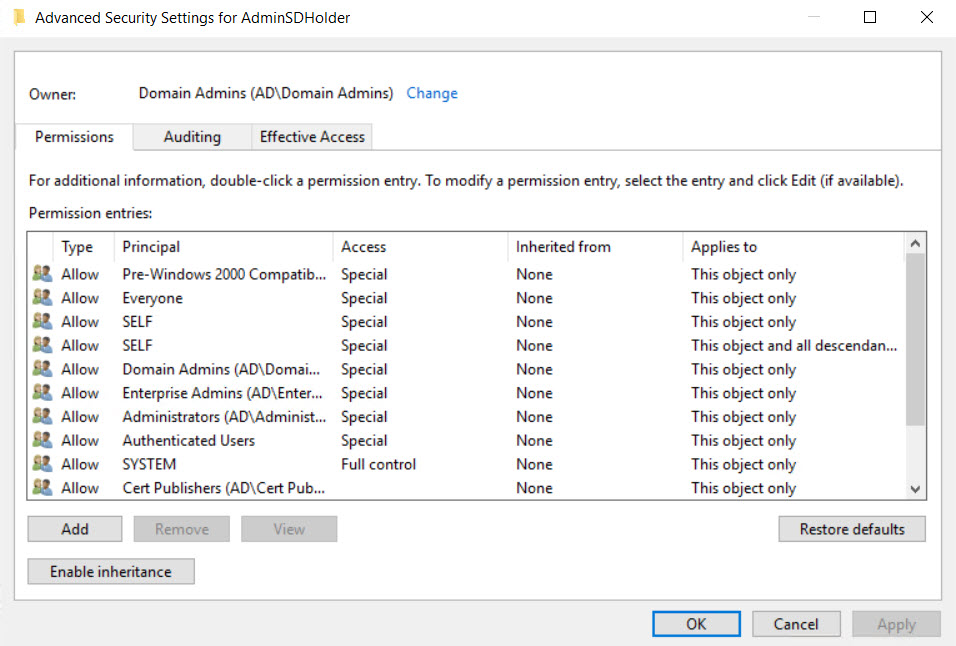
Some privileged groups can be excluded from protection. You might want to remove a group, like Print Operators, if you have modified the group to remove its privileged access to AD. To change which groups are protected, change the dsHeuristics attribute in CN=Directory Service,CN=Windows NT,CN=Services,CN=Configuration,DC=ad,DC=contoso,DC=com. To access the Directory Service container, open ADSI Edit from the Tools menu in Server Manager and connect to Configuration. Right-click CN=Directory Service on the left and then select Properties from the menu. Scroll down the list of the attributes in the Properties dialog until you find dsHeuristics.
Each of the four groups that can be excluded from SDPROP has a binary value as shown in the table below:
| Group | Binary | Hexadecimal |
| Account Operators | 0001 | 1 |
| Server Operators | 0010 | 2 |
| Print Operators | 0100 | 4 |
| Backup Operators | 1000 | 8 |
The dwAdminSDExMask controls which of the above groups is excluded from SDPROP. The dwAdminSDExMask is the 16th bit of the value set in dsHeuristics and is a hexadecimal value. So, if you want to exclude Print Operators from SDPROP, the 16th bit should be set to 4. The value for dsHeuristics would look like this:
0000000001000004
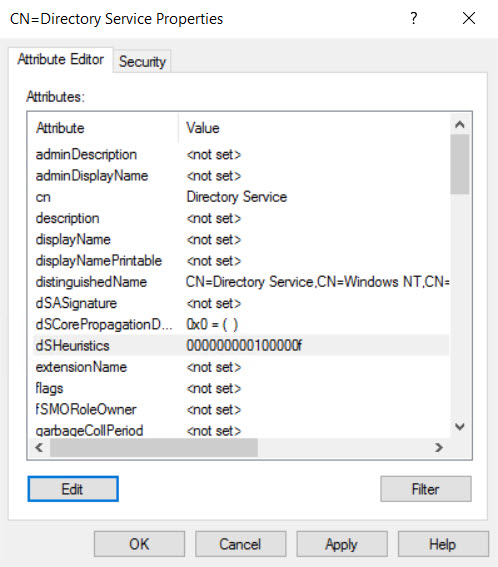
The 10th bit is always set to 1 if the value is longer than 10 bits. If you only want to modify dwAdminSDExMask, only change the 16th bit. Leave all other bits alone. If you want to exclude more than one group, add the binary values together and then convert the result to hex, for example, to exclude Backup Operators, Print Operators, Server Operators, and Account Operators:
0001 + 0010 + 0100 + 1000 = 1111
1111 = f
So, the dsHeuristics would look like this:
000000000100000f
Discover Users with Blocked Inheritance
If you want to find out which users in a domain have inheritance blocked, there’s a PowerShell script in the TechNet gallery which enumerates user objects in each Organizational Unit (OU), checks to see if inheritance is disabled on each object, and then dumps the results to a comma-delimited file (.csv). You can download the script here.
In this Ask the Admin, I explained how adminSDHolder is used to protect privileged AD accounts and how you can modify it to exclude some privileged groups from protection and change the frequency of SDPROP.




