SubInACL Permission Types
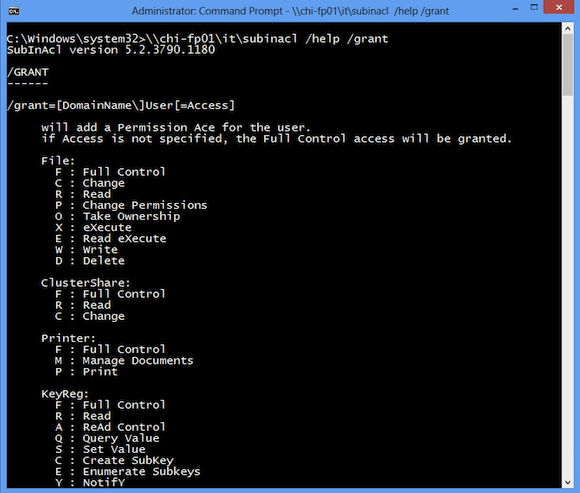
You can use subinacl.exe to manage permissions on a variety of object types. The permission setting varies depending on the object. You can find the permission values with this command.
C:\> subinacl /help /grant
In the screen shot, I am running subinacl.exe from a network share. All I had to do was copy just the exe file.
In order for this to work, I am running the CMD session with elevated privileges. Use the correct permission abbreviation for the object you wish to manage.
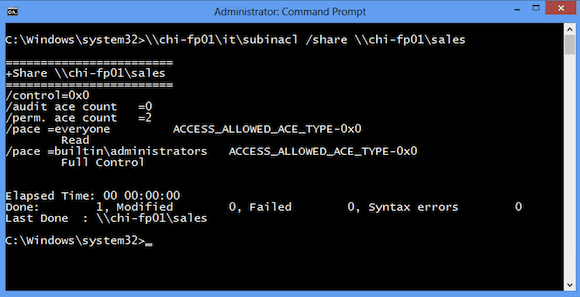
SubInACL File Share Example
From my Windows 8 system, I can see the current share permission for \\CHI-FP01\Sales.
C:\Windows\system32>\\chi-fp01\it\subinacl /share \\chi-fp01\sales
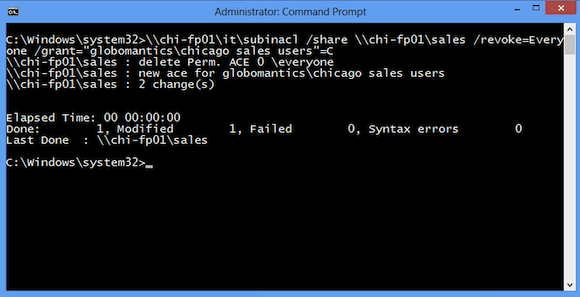
I want to remove the Everyone group and grant the Chicago Sales Users group change permission. I can do this with a single command:
C:\Windows\system32>\\chi-fp01\it\subinacl /share \\chi-fp01\sales /revoke=Everyone /grant="globomantics\chicago sales users"=C
From PowerShell I can quickly verify this change.
PS C:\> invoke-command {net share Sales} -ComputerName chi-fp01
Share name Sales
Path c:\shares\Sales
Remark
Maximum users No limit
Users
Caching Manual caching of documents
Permission BUILTIN\Administrators, FULL
GLOBOMANTICS\chicago sales users, CHANGE
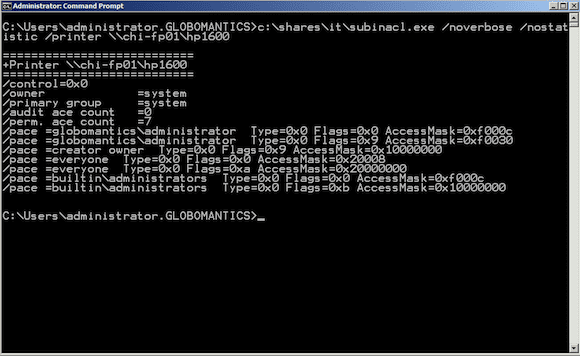
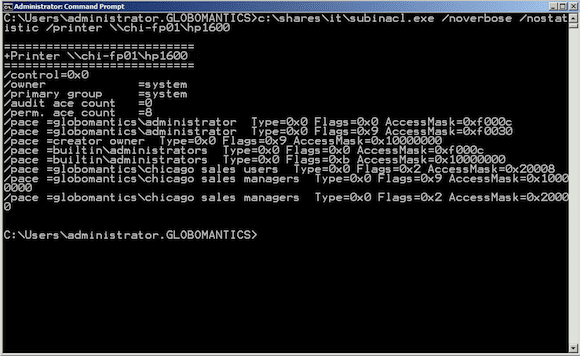
SubInACL Printer Share Example
This will also work with shared printers. First, here’s the current set of permissions for the printer share \\CHI-FP01\HP1600.
C:\Users\administrator.GLOBOMANTICS>c:\shares\it\subinacl.exe /noverbose /nostatistic /printer \\chi-fp01\hp1600
In this particular case I am running SubInACL on the print server. Sometimes you’ll get an RPC error even though everything is working correctly, so it is just as easy to run the command locally. I need to remove the Everyone group, grant Chicago Sales Users the option to print, and Chicago Sales Managers permission to manage documents.
C:\Users\administrator.GLOBOMANTICS>c:\shares\it\subinacl.exe /noverbose /nostatistic /printer \\chi-fp01\hp1600 /revoke=everyone /grant="globomantics\chicago sales users"=P /grant="globomantics\chicago sales managers"=M
I found the permission types from looking at help.
Printer: F : Full Control M : Manage Documents P : Print
Now when I look at permissions again, they are as I need them to be.
Clearing Permissions
There is one more setting I’ll discuss because it is very easy to make things worse with subinacl.exe. When you look through help you’ll see a /perm action. You might think this will display current permissions. This is not the case and where you have to be careful. When you use /perm, subinacl will wipe out all existing permissions. This has the effect of resetting to a blank state, with the assumption that you will be immediately setting new permissions. The action can certainly be helpful if that is what you intend to do.
Subinacl.exe is worth exploring in a non-production environment. I would also make sure any existing permissions are documented before applying any changes. Over the last decade Microsoft has given us new tools to handle many of the tasks that we used handle with subinacl.exe. But for those exceptions, this is a tool still worth keeping in your admin toolbelt. And if subinacl has ever solved a problem for you, leave a comment below and let me know how it worked out.