Create and Log Your Own Events – Part 1
Overview
I’m sure you’ve used the event logs in Windows on more than one occasion. They are an invaluable resource for IT Pros when it comes to troubleshooting, analyzing or reporting. But did you know you can create your own event log entries? It doesn’t even require any programming or scripting. Perhaps you want to write an entry to the System event log when you run some sort of audit process. Perhaps you need an entry in the Application log to reflect the installation of an in-house application. Or perhaps you simply want to “touch” an event log.
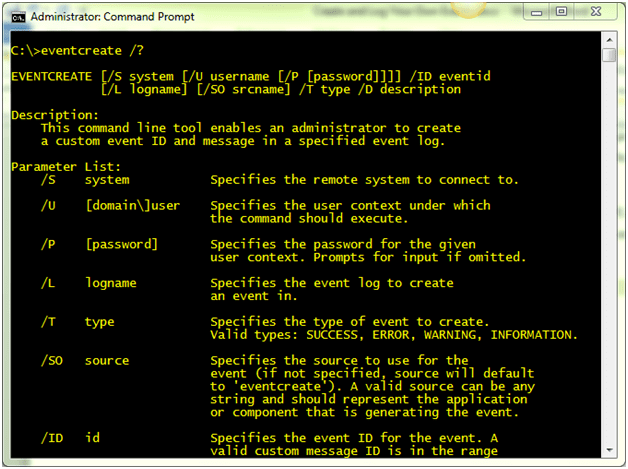
On your Windows 7 desktop, you can use the command line utility, EVENTCREATE.EXE. This utility can create event log entries locally as well as on remote computers. Use the typical command line syntax to get help.
C:\> eventcreate /?
Figure 1 EventCreate.exe Help
Let’s try this out locally. You must specify at least the type (/T) and id (/id).
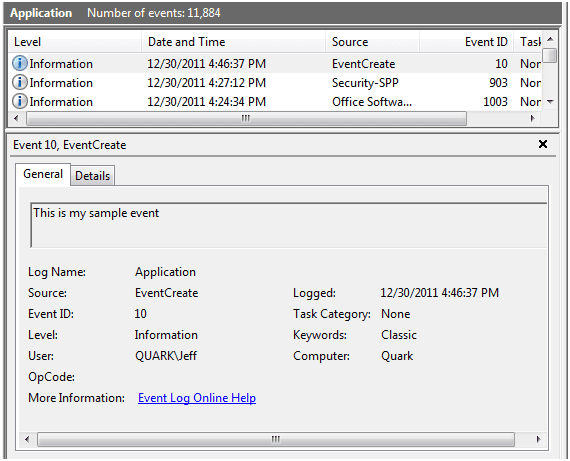
C:\>eventcreate /d "This is my sample event" /t information /id 10 SUCCESS: An event of type 'information' was created in the 'Application' log with 'EventCreate' as the source.
The default log is Application and the default source is “EventCreate”.Figure 2 shows what the event looks like.
Figure 2 A New Event
The ID number can be whatever you need it to be. Let’s create another event locally.
C:\>eventcreate /l System /id 900 /so Private /d "Internal Audit Complete" /t Information SUCCESS: An event of type 'Information' was created in the 'System' log with 'Private' as the source.
What I like about this tool is that you can use either an established source or define your own. However, you cannot write custom events to the Security log.
C:\>eventcreate /t warning /d Oops /l security /id 100 ERROR: Access is denied. Custom events cannot be created into security log.
The utility will use your current credentials, but you can specify alternate credentials using the /U and /P parameters. This makes more sense when writing entries to remote logs. You can use it locally, but you’ll get a warning message. Here’s how I might create an entry on a remote computer.
C:\>eventcreate /t warning /id 55 /l Application /s File01 /u mycompany\jeff /p P@ssw0rd /d "User profile doesn't meet company standards" /so MyCompany SUCCESS: An event of type 'warning' was created in the 'Application' log with 'MyCompany' as the source.
If you don’t want to type the password in clear text, you can use /p without any values and you’ll be prompted for the password.
C:\>eventcreate /t warning /id 55 /l Application /s WinDesk02 /u mycompany\jeff /p /d "User profile doesn't meet company standards" /so MyCompany Type the password for mycompany\jeff:********** SUCCESS: An event of type 'warning' was created in the 'Application' log with 'MyCompany' as the source.
Conclusion
If you plan on using EVENTCREATE.EXE, I encourage you to document how and where you intend to use it. Define a list of source names, entry types and corresponding ID codes.
Next time I’ll show you how to accomplish custom event log entries using Windows PowerShell.